10 Fort Knox Strategies: Guarding Your Business Against Cyber Raiders
The digital frontier, once a Wild West of opportunity, is now patrolled by sophisticated cyber raiders. They’re after your data, your reputation, and ultimately, your business. But fear not! This isn’t a hopeless battle. Armed with these 10 “Fort Knox” strategies, you can build an impenetrable defense and safeguard your digital kingdom.
1. Embrace the Zero Trust Mindset: Assume Breach!
Forget the outdated “castle walls” approach. Instead, envision every user, every device, and every network segment as potentially compromised. The Zero Trust model verifies everything before granting access.
| Traditional Security | Zero Trust Security |
|---|---|
| Trust but verify (once) | Never trust, always verify |
| Perimeter-focused | Data and resource-focused |
| Vulnerable to insider threats | Minimizes lateral movement |
Implementation: Implement Multi-Factor Authentication (MFA) rigorously. Segment your network to limit the blast radius of any potential breach. Regularly audit user access rights.
2. Phishing: The Siren Song of Cybercrime – Train Your Crew!
Phishing attacks, disguised as legitimate emails or messages, are the gateway drug for many cyberattacks. Education is your best weapon.
| Phishing Tactic | Red Flag |
|---|---|
| Urgent requests for information | Suspicious sender, unusual attachments |
| Suspicious links | Mismatched URLs |
| Generic greetings | Poor grammar and spelling |
Implementation: Conduct regular phishing simulations. Provide comprehensive employee training on recognizing and reporting phishing attempts. Foster a culture of “question everything.”
3. Patch Your Armor: Keep Software Updated!
Outdated software is a gaping wound in your defenses. Cybercriminals exploit known vulnerabilities in unpatched systems like they’re going out of style.
| Software Type | Frequency |
|---|---|
| Operating Systems | Immediately (or set up automatic updates) |
| Applications (Office Suite, Browsers) | Regularly, as updates are released |
| Security Software | Automatic Updates are crucial |
Implementation: Implement automated patching systems. Prioritize critical patches based on severity and known exploits. Have a system for testing updates before widespread deployment.
4. Password Hygiene: Fortify Your Digital Keys!
Weak passwords are an invitation to your digital vault. Enforce strong password policies and practice good password management.
| Password Weakness | Solution |
|---|---|
| Short passwords | Minimum 12-16 characters |
| Easily guessed passwords | Use a password manager |
| Reuse of passwords | Unique password for each account |
Implementation: Mandate strong, complex passwords (length and complexity). Utilize password managers for secure storage and generation. Enforce regular password changes (every 90 days or less). Use MFA whenever possible.
5. Data Backup: The Life Raft in a Digital Storm!
Ransomware attacks can cripple your business. Having a reliable backup plan is crucial for data recovery.
| Backup Strategy | Key Benefit |
|---|---|
| 3-2-1 Rule: 3 copies of your data, 2 on different media, 1 offsite. | Disaster Recovery, Business Continuity |
| Immutable Backups | Protect against ransomware |
| Regular Testing | Ensures backups are functional |
Implementation: Implement a robust backup strategy following the 3-2-1 rule. Test your backups regularly (at least quarterly) to ensure data restoration is possible. Verify and test Immutable Backups to keep your data safe from ransomware.
6. Network Segmentation: Contain the Breach!
Divide your network into isolated segments. This limits the damage a successful attack can inflict by preventing attackers from freely moving throughout your system.
| Network Segment Example | Purpose |
|---|---|
| Employee workstations | Restricted access to sensitive data |
| Servers | Hosting critical applications |
| Guest network | Isolated from internal resources |
Implementation: Segment your network using firewalls and virtual LANs (VLANs). Implement strict access controls between segments. Monitor network traffic for suspicious activity.
7. Endpoint Detection and Response (EDR): Vigilant Watchdogs!
EDR solutions go beyond traditional antivirus to proactively detect and respond to threats on individual devices (endpoints).
| EDR Capability | Benefit |
|---|---|
| Threat detection & analysis | Identifies suspicious behavior |
| Incident response | Automated remediation & containment |
| Forensic investigation | Analyzes attack details |
Implementation: Deploy an EDR solution on all endpoints (laptops, desktops, servers). Configure EDR to automatically quarantine suspicious files and processes. Regularly review EDR alerts and logs.
8. Security Information and Event Management (SIEM): Your Central Command!
A SIEM solution collects and analyzes security data from various sources, providing a centralized view of your security posture.
| SIEM Function | Benefit |
|---|---|
| Log aggregation & analysis | Identifies anomalies and trends |
| Security monitoring & alerting | Real-time threat detection |
| Compliance reporting | Demonstrates security effectiveness |
Implementation: Implement a SIEM solution. Integrate your firewalls, EDR, and other security tools. Configure alerts for critical events. Review SIEM dashboards regularly.
9. Incident Response Plan: Prepare for the Inevitable!
Even with the best defenses, breaches can happen. Having a well-defined incident response plan is critical for minimizing damage and restoring operations quickly.
| Incident Response Phase | Action |
|---|---|
| Preparation | Develop plan, train staff, set up communication channels |
| Identification | Detect and confirm the incident |
| Containment | Limit the spread of the attack |
| Eradication | Remove the threat |
| Recovery | Restore systems and data |
| Post-Incident Activity | Learn from the incident, improve defenses |
Implementation: Develop a comprehensive incident response plan. Conduct tabletop exercises to test the plan’s effectiveness. Regularly review and update the plan based on lessons learned.
10. Stay Informed: Knowledge is Power!
The cyber threat landscape is constantly evolving. Stay up-to-date on the latest threats, vulnerabilities, and best practices.
| Information Source | Benefit |
|---|---|
| Security blogs & newsletters | Latest threat intelligence |
| Industry conferences & webinars | Learn from experts |
| Government resources (NIST, CISA) | Best practices and guidance |
Implementation: Subscribe to security blogs and newsletters. Attend industry conferences and webinars. Review government resources for best practices and guidance. Cultivate a culture of continuous learning within your team.
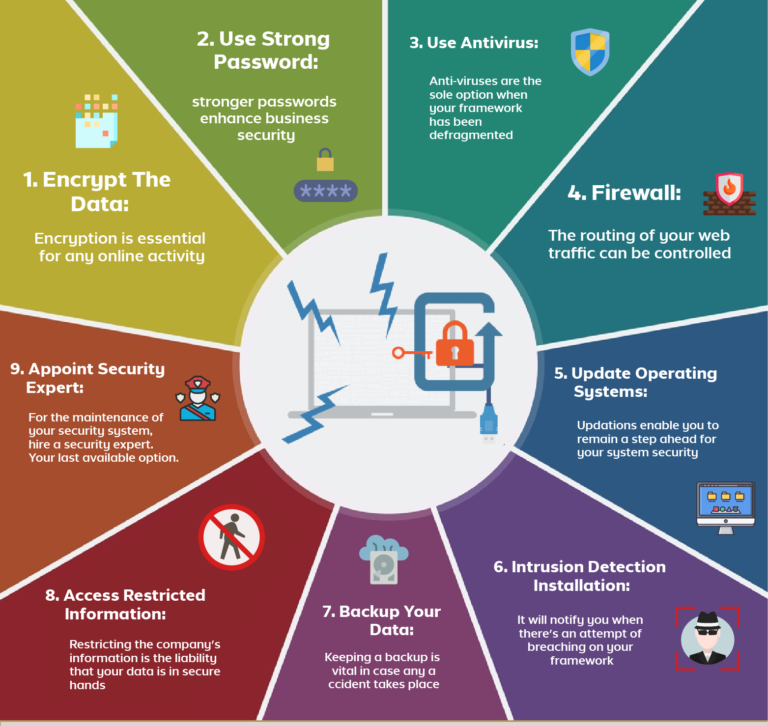
Additional Information
10 Best Practices for Securing Your Business from Cyber Attacks: A Detailed Analysis
Here’s a breakdown of the 10 best practices for securing your business from cyberattacks, delving into their importance and providing detailed insights:
1. Implement a Strong Password Policy and Multi-Factor Authentication (MFA):
- Detailed Explanation: This is the foundation of good security. A strong password policy requires:
- Length: Passwords should be at least 12-16 characters long, ideally longer.
- Complexity: Incorporate a mix of uppercase and lowercase letters, numbers, and special characters. Avoid easily guessable information like personal details (birthdays, pet names) or dictionary words.
- Regular Rotation: Change passwords periodically (every 90 days is a common recommendation), but focus more on security incidents and when suspicious activity is noticed.
- Password Managers: Encourage the use of password managers (like LastPass, 1Password, or Bitwarden) to generate and securely store complex, unique passwords for each account.
- MFA Significance: MFA adds an extra layer of security beyond passwords. It requires users to provide a second form of verification (e.g., a code from a mobile app, a security key, or a biometric scan) in addition to their password. This significantly reduces the risk of compromised accounts, even if passwords are stolen.
- Analysis: Compromised passwords are a primary attack vector. MFA dramatically increases the difficulty for attackers to gain unauthorized access. Without MFA, a stolen password grants full access.
- Implementation Steps:
- Enforce password policies through your Active Directory, cloud platforms (e.g., Microsoft 365, Google Workspace), and other systems.
- Deploy MFA across all critical systems (email, VPN, financial platforms, etc.).
- Educate employees on creating strong passwords and the importance of MFA.
- Regularly audit password strength and compliance.
2. Regularly Update Software and Systems:
- Detailed Explanation: Software updates (including operating systems, applications, firmware on devices) patch security vulnerabilities that attackers exploit. This includes:
- Operating Systems (Windows, macOS, Linux): Critical security updates must be applied promptly.
- Applications (Browsers, Office Suites, PDF Readers): These are frequent targets. Enable automatic updates where possible.
- Firmware (Routers, Firewalls, IoT devices): Often overlooked but crucial. Regularly check the manufacturer’s website for firmware updates.
- Vulnerability Scanning: Implement a vulnerability scanner to proactively identify outdated software and systems with known vulnerabilities.
- Analysis: Exploiting known vulnerabilities is a common attack method. Failing to update leaves your systems exposed to known exploits, making them easy targets.
- Implementation Steps:
- Establish a patching schedule and process (weekly or bi-weekly).
- Test updates in a non-production environment before deploying them to production systems.
- Use patch management tools to automate and streamline the patching process.
- Monitor for and address zero-day vulnerabilities (vulnerabilities discovered before a patch is available) by applying workarounds or implementing compensating controls.
3. Train Employees on Security Awareness:
- Detailed Explanation: Human error is a significant factor in cyberattacks. Security awareness training educates employees about common threats and best practices:
- Phishing Awareness: Teach employees to identify phishing emails (look for suspicious senders, grammatical errors, unexpected attachments or links, urgency). Conduct simulated phishing campaigns to test employee awareness and identify areas for improvement.
- Social Engineering: Explain how attackers use social engineering techniques to trick employees into divulging sensitive information or granting access to systems (e.g., pretexting, baiting, quid pro quo).
- Password Security: Reinforce the importance of strong passwords, password managers, and avoiding password reuse.
- Data Security: Educate employees on handling sensitive data (Personally Identifiable Information – PII, financial data, intellectual property). Explain data classification policies and secure data storage practices.
- Reporting Security Incidents: Establish a clear process for employees to report suspicious activity (phishing emails, data breaches, compromised devices).
- Analysis: Employees are often the “weakest link” in cybersecurity. Training empowers them to recognize and avoid threats, reducing the risk of successful attacks.
- Implementation Steps:
- Develop a comprehensive security awareness training program (online modules, workshops, quizzes).
- Deliver training regularly (at least annually, ideally more frequently).
- Use real-world examples and scenarios to make training relevant and engaging.
- Track training completion and assess employee knowledge through quizzes and simulated attacks.
4. Implement a Robust Firewall and Network Segmentation:
- Detailed Explanation:
- Firewall: A firewall acts as a barrier, monitoring and controlling network traffic based on predefined rules. It protects your network from unauthorized access and malicious traffic.
- Network Segmentation: Divide your network into isolated segments (e.g., separating your production servers from your employee workstations, or separating guest Wi-Fi from your internal network). This limits the impact of a security breach. If one segment is compromised, the attacker’s ability to move laterally through the network is restricted.
- Analysis: Firewalls prevent unauthorized access from outside your network and can block malicious traffic. Network segmentation limits the scope of a breach.
- Implementation Steps:
- Deploy a firewall at your network perimeter (at the edge of your network) and potentially internal firewalls to segment your network.
- Configure firewall rules to allow only necessary traffic and block all other traffic.
- Regularly review and update firewall rules to adapt to changing threats.
- Use a network intrusion detection system (NIDS) or intrusion prevention system (NIPS) to monitor network traffic for suspicious activity.
- Implement micro-segmentation for zero-trust architectures.
5. Back Up Data Regularly and Test Backups:
- Detailed Explanation: Backups are crucial for data recovery in case of ransomware attacks, hardware failures, accidental data deletion, or other disasters.
- Backup Strategy: Implement a comprehensive backup strategy:
- Frequency: Determine the optimal backup frequency based on the criticality of your data (daily, hourly, or more frequently).
- Types: Use a combination of full, incremental, and differential backups.
- Location: Store backups in a secure, offsite location (cloud-based backups are often a good option, alongside local backups for faster recovery of critical systems).
- Automation: Automate the backup process to minimize the risk of human error.
- Testing Backups: Regularly test your backups by restoring data to ensure they are working correctly and that you can recover your systems and data in a timely manner.
- Backup Strategy: Implement a comprehensive backup strategy:
- Analysis: Backups are your last line of defense against data loss. They are essential for business continuity. Ransomware attacks increasingly target backup systems, so securing backups is crucial.
- Implementation Steps:
- Develop a detailed backup and recovery plan.
- Choose a backup solution that meets your needs and budget.
- Automate backups and test them regularly (at least quarterly, ideally more often).
- Encrypt backups to protect data confidentiality.
- Implement the “3-2-1” rule: 3 copies of your data, on 2 different media, with 1 offsite.
6. Control Access to Sensitive Data and Systems:
- Detailed Explanation: Implement the principle of least privilege. Grant users only the minimum level of access necessary to perform their job duties.
- Role-Based Access Control (RBAC): Assign users to roles with specific permissions (e.g., “Administrator,” “Salesperson,” “Customer Service Representative”).
- Access Control Lists (ACLs): Use ACLs to define who can access specific files, folders, and resources.
- Regular Access Reviews: Periodically review user access rights to ensure they are still appropriate. Remove access for employees who have left the company or whose roles have changed.
- Data Loss Prevention (DLP): Implement DLP solutions to monitor and control the movement of sensitive data within your organization (e.g., preventing users from emailing confidential documents outside the organization).
- Analysis: Limiting access reduces the potential damage from a compromised account. A user with limited access can’t cause as much harm as a user with broad administrative rights.
- Implementation Steps:
- Implement RBAC across all systems and applications.
- Use ACLs to protect sensitive data.
- Regularly review user access rights (at least annually, or more frequently).
- Use DLP to monitor and control data movement.
- Implement a zero-trust access model.
7. Monitor and Log Security Events:
- Detailed Explanation: Implement security information and event management (SIEM) tools to collect, analyze, and correlate security event data from various sources (firewalls, servers, applications, intrusion detection systems, etc.).
- Log Collection: Collect logs from all relevant systems and applications.
- Log Analysis: Use SIEM tools to analyze logs for suspicious activity, such as failed login attempts, unusual network traffic, or changes to system configurations.
- Alerting: Configure SIEM tools to generate alerts when suspicious events are detected.
- Incident Response: Establish an incident response plan to handle security incidents effectively.
- Analysis: Monitoring and logging provide visibility into your security posture and allow you to detect and respond to security incidents quickly.
- Implementation Steps:
- Deploy a SIEM solution.
- Configure SIEM tools to collect logs from all relevant sources.
- Define and implement alerting rules to detect suspicious activity.
- Establish an incident response plan.
- Regularly review and refine alerting rules based on threat intelligence.
8. Use Endpoint Detection and Response (EDR) Solutions:
- Detailed Explanation: EDR solutions provide advanced threat detection and response capabilities on endpoints (desktops, laptops, servers).
- Real-time Monitoring: Monitor endpoint activity in real-time for suspicious behavior.
- Threat Detection: Use behavioral analysis, machine learning, and threat intelligence to detect known and unknown threats.
- Incident Response: Provide tools to investigate and respond to security incidents on endpoints (e.g., isolating infected endpoints, killing malicious processes, quarantining files).
- Endpoint Protection Platform (EPP): EDR solutions often integrate with EPP solutions (antivirus, firewalls, application control) for a comprehensive endpoint security approach.
- Analysis: EDR solutions provide visibility into endpoint activity, which is often a critical entry point for attackers. They enable rapid detection and response to threats, reducing the impact of attacks.
- Implementation Steps:
- Select an EDR solution that meets your needs and budget.
- Deploy the EDR solution on all endpoints.
- Configure EDR settings to optimize threat detection and performance.
- Train security staff on using EDR tools to investigate and respond to security incidents.
- Integrate EDR with your SIEM solution for centralized monitoring and alerting.
9. Secure Remote Access:
- Detailed Explanation: With the increasing prevalence of remote work, securing remote access is more important than ever.
- Virtual Private Network (VPN): Use a VPN to encrypt all network traffic between remote users and your network. This protects data in transit.
- Multi-Factor Authentication (MFA): Require MFA for all remote access methods (VPN, remote desktop, cloud applications).
- Least Privilege Access: Limit remote users’ access to only the resources they need to perform their work.
- Device Security: Ensure that remote devices are secure (e.g., with up-to-date software, antivirus, and a firewall).
- Remote Access Policies: Develop and enforce remote access policies that define acceptable use, security requirements, and procedures for reporting security incidents.
- Analysis: Remote access can create new attack vectors. Securing remote access protects your network from unauthorized access and data breaches.
- Implementation Steps:
- Implement a VPN for secure remote access.
- Require MFA for all remote access.
- Implement least privilege access.
- Ensure remote devices are secured.
- Develop and enforce remote access policies.
10. Develop and Regularly Review an Incident Response Plan:
- Detailed Explanation: An incident response plan outlines the steps your organization will take to respond to a security incident (e.g., a data breach, a ransomware attack).
- Preparation: Develop an incident response plan, define roles and responsibilities, and conduct training and exercises.
- Identification: Detect and identify security incidents (e.g., through security monitoring, employee reports).
- Containment: Limit the scope of the incident to prevent further damage (e.g., isolate infected systems, block malicious traffic).
- Eradication: Remove the cause of the incident (e.g., remove malware, patch vulnerabilities).
- Recovery: Restore affected systems and data.
- Post-Incident Activity: Learn from the incident, update security measures, and improve the incident response plan.
- Analysis: An incident response plan helps your organization respond to security incidents effectively and minimize the damage.
- Implementation Steps:
- Develop a detailed incident response plan.
- Define roles and responsibilities for incident response team members.
- Conduct regular training and exercises to test the plan and ensure that team members are prepared.
- Review and update the plan regularly to adapt to changing threats.
- Maintain communication channels for incident reporting and communication during an event.
By implementing these 10 best practices, businesses can significantly improve their security posture, protect themselves from cyberattacks, and minimize the potential impact of security incidents. Remember that cybersecurity is an ongoing process, not a one-time fix. Regularly review and update your security measures to adapt to the evolving threat landscape.





