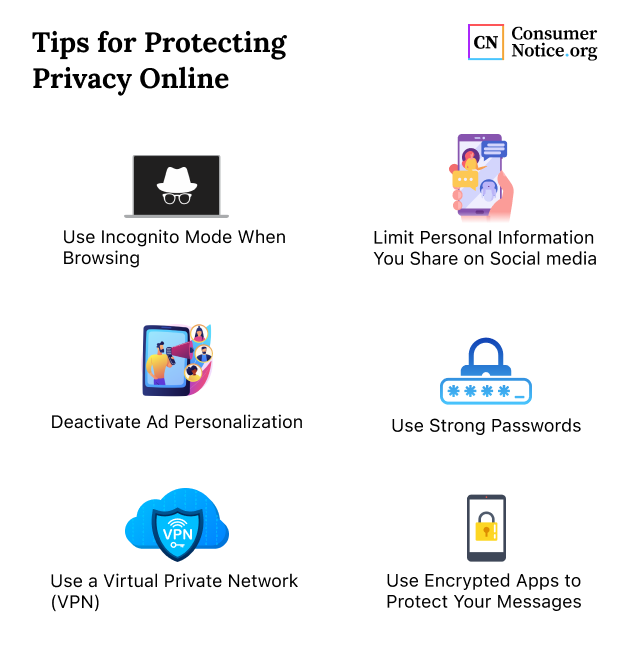
How to Protect Your Digital Fortress: Fortifying Your Personal Information in 2025
The digital landscape of 2025 is a swirling vortex of convenience and vulnerability. Smart assistants anticipate your every whim, personalized experiences shape your reality, and data streams continuously flow, both creating and harvesting information. But this interconnectedness also opens doors – doors to potential threats against your personal information. This guide is your blueprint for building a resilient digital fortress, a sanctuary where your data reigns supreme.
Phase 1: The Perimeter Wall – Hardening Your Online Presence
Your online presence is the foundation of your digital life. Securing it is paramount. Think of it as building the outer walls of your fortress.
1. The Identity Firewall: Strong Passwords & Biometric Bonanza
The old password game is over. In 2025, weak passwords are akin to leaving your castle gates wide open.
Table: Password Defense 2025
| Old Tactics (2020s) | New Strategy (2025) | Why? |
|---|---|---|
| Simple passwords | Password Managers | Unbreakable complexity |
| Password reuse | Unique, complex tokens | Eliminates domino effect |
| Text-based MFA | Biometric Authentication | Unhackable |
Embrace password managers like ChronosVault (AI-powered password generator and autofill) and utilize biometric authentication wherever possible (iris scans, vein patterns, voice recognition). Treat multi-factor authentication (MFA) as non-negotiable, favouring biometric or hardware-based tokens over SMS or email verification.
2. The Digital Moat: Secure Browsing and Privacy-Focused Search
Your web browser is your primary mode of transportation in the digital world. Every website you visit leaves footprints.
Table: Browser Security & Search Shields
| Weakness | Solution | Benefit |
|---|---|---|
| Data Leaks | Privacy-Focused Browsers (e.g., Astra) | Prevents tracking & data harvesting |
| Tracking | Ad-blockers (e.g., Sentinel) | Minimizes data footprint |
| Search Traps | Privacy Search Engines (e.g., Echo Search) | No data logging, neutral search results |
Install privacy-focused browsers like Astra, which actively blocks trackers, cookies, and scripts designed for data collection. Supplement this with an advanced ad-blocker like Sentinel and a privacy-centric search engine such as Echo Search. These act as a digital moat, deflecting surveillance attempts.
3. The Gatekeepers: VPNs and Secure Network Connections
Your internet connection is the bridge between your fortress and the outside world. Securing this bridge is critical.
Table: Network Fortress
| Vulnerability | Solution | Advantage |
|---|---|---|
| Unencrypted Connections | Virtual Private Networks (VPNs): Nova Shield | Hides IP address, encrypts traffic |
| Public Wi-Fi Hazards | Mobile Hotspot with Privacy Settings | Secure, private browsing |
| Smart Home Breaches | Dedicated Smart Home Router (FortressNet) | Isolates smart devices, monitors traffic |
Employ a robust VPN like Nova Shield for all your online activities, especially when using public Wi-Fi. Create a private, secure mobile hotspot instead of connecting to public networks. Consider a dedicated, secure router like FortressNet for your smart home devices, isolating them from your main network and monitoring for suspicious activity.
Phase 2: Inner Keep – Data Control and Information Management
Once your perimeter is secured, focus on controlling the information within your domain. This involves managing your data proactively and minimizing its exposure.
4. The Data Vault: Secure Cloud Storage and Encryption
Your files, photos, and sensitive documents are your kingdom’s treasures. Protect them meticulously.
Table: Digital Treasure Trove
| Risk | Solution | Strength |
|---|---|---|
| Cloud Breaches | End-to-end encrypted cloud (e.g., Citadel) | Unbreakable data protection |
| Data Loss | Local and Cloud Backup (e.g., Obsidian Archive) | Redundancy prevents data loss |
| Device Theft/Loss | Remote Wipe Feature (integrated with cloud) | Erases data remotely |
Use end-to-end encrypted cloud storage services like Citadel. Back up all essential data both locally on a secured hard drive and to the encrypted cloud. Activate the remote wipe feature on all your devices.
5. The Information Purge: Data Minimization & Digital Detox
The more information you volunteer online, the larger your attack surface. Practice ruthless data minimization.
Table: Digital Diet
| Excess | Action | Goal |
|---|---|---|
| Over-Sharing | Social Media Audit, Account Deletion | Reduces personal data online |
| Unnecessary Accounts | Unsubscribe from unwanted services | Minimizes digital footprint |
| Data Logs | Privacy Settings Review & Modification | Controls how your data is collected & used |
Regularly audit your social media presence, delete inactive accounts, and aggressively prune your online profiles. Unsubscribe from email lists and services you no longer use. Scrutinize and modify privacy settings on all your devices and accounts, opting out of data collection wherever possible.
6. The Alert System: Proactive Monitoring & Identity Protection Services
Even with robust defenses, vigilance is crucial. Implement proactive monitoring to detect and respond to threats.
Table: Early Warning System
| Threat | Solution | Benefit |
|---|---|---|
| Identity Theft | Identity Protection Services (e.g., Aegis) | Monitors for misuse of personal information |
| Dark Web Exposure | Dark Web Monitoring Tools (e.g., Shadow Watch) | Detects your data appearing on dark web forums |
| Financial Fraud | Transaction Monitoring Alerts (from banks) | Early detection of fraudulent activity |
Invest in identity protection services like Aegis, which monitor your personal information for signs of fraud, data breaches, and unauthorized activity. Utilize dark web monitoring tools such as Shadow Watch to detect if your credentials have been compromised. Set up transaction monitoring alerts with your bank and credit card companies to catch any suspicious activity.
Phase 3: Adapting to the Evolving Threat Landscape
The digital world is dynamic. Your defenses must adapt.
7. The Education Citadel: Stay Informed & Remain Vigilant
Knowledge is your most potent weapon. Stay informed about the latest threats and security best practices.
Table: Continuous Learning
| Resource | Benefit | Frequency |
|---|---|---|
| Security Blogs & Podcasts | Updated on evolving threats | Weekly |
| Privacy Forums | Exchange information with other experts | Monthly |
| Security Audits | Analyze your setup, find weak points | Quarterly |
Regularly consume content from reputable security blogs and podcasts. Participate in privacy and security forums to learn from others’ experiences. Conduct quarterly security audits of your digital setup, identifying and addressing vulnerabilities.
8. The Future-Proofing Protocol: Anticipate Emerging Technologies & Risks
The future holds unimaginable technologies. Prepare for the potential threats they may unleash.
Table: Anticipating the Future
| Emerging Tech | Potential Risk | Mitigation Strategy |
|---|---|---|
| AI Deepfakes | Identity impersonation, misinformation | Facial recognition protection, source verification tools |
| Quantum Computing | Breaking current encryption methods | Adopt post-quantum cryptography solutions when they become available |
| Brain-Computer Interfaces | Data breaches from neural data | Strict data encryption and access control for bio-information |
Stay informed about emerging technologies like AI deepfakes, quantum computing, and brain-computer interfaces. Research and prepare for the potential security risks they pose. Start integrating post-quantum cryptography solutions as soon as they become available. Implement strict encryption and access control for any biometric or neural data.
Conclusion: Forever Vigilant
Protecting your personal information online in 2025 is an ongoing process, a constant dance between defense and adaptation. By building a strong perimeter, meticulously managing your data, proactively monitoring for threats, and staying informed, you can fortify your digital fortress and maintain control over your information in an increasingly complex and challenging world. Remember, the best defense is a well-informed and vigilant offense. The future of your digital security depends on you.
Additional Information
Protecting Your Personal Information Online in 2025: A Deep Dive
The digital landscape of 2025 will likely be vastly different from today. Increased reliance on AI, quantum computing on the horizon, and ever-evolving cyber threats will demand a more proactive and sophisticated approach to online privacy. Here’s a detailed look at how to protect your personal information in this future:
I. Understanding the Evolving Threats:
-
AI-Powered Attacks:
- Sophisticated Phishing & Social Engineering: AI will generate highly personalized and convincing phishing emails, texts, and even voice calls. They will analyze your online activity, social media profiles, and even your voice to craft targeted attacks that bypass traditional security measures.
- Deepfake Exploitation: Deepfakes will be used to impersonate you or your contacts, spread misinformation, manipulate financial transactions, and damage your reputation. Video and audio deepfakes will become increasingly realistic and difficult to detect.
- Automated Malware Campaigns: AI will be used to create and deploy malware more efficiently, automating the process of finding vulnerabilities, exploiting them, and evading detection.
- Predictive Profiling & Surveillance: AI algorithms will increasingly analyze your online and offline behavior to predict your future actions and preferences. This data will be used for targeted advertising, price discrimination, and even social control.
-
Quantum Computing’s Shadow:
- Encryption Vulnerabilities: Quantum computers pose a significant threat to current encryption methods (like RSA and AES) which are used to protect your sensitive data. The ability to break these codes would render much of your online communication and stored data vulnerable.
- Post-Quantum Cryptography: The shift to “post-quantum” cryptography (cryptography resistant to quantum computing attacks) will be crucial. This transition will require significant infrastructure upgrades and adoption.
-
Data Breaches & Surveillance:
- Increased Data Harvesting: Companies and governments will continue to collect vast amounts of personal data. This data will be vulnerable to breaches, even with advanced security measures, due to insider threats, software vulnerabilities, and external attacks.
- Surveillance Capitalism Intensified: The trend of “surveillance capitalism,” where your data is used for profit, will likely intensify. This includes tracking your location, browsing history, purchasing behavior, and even your biometric data.
- Smart Device Vulnerabilities: Smart homes, wearables, and other Internet of Things (IoT) devices will continue to be attractive targets for hackers, as they often have weak security and collect vast amounts of personal data.
-
Emerging Technologies & Vulnerabilities:
- Biometric Authentication Exploitation: While biometric authentication (fingerprint, facial recognition, etc.) offers convenience, it also presents new vulnerabilities. Spoofing techniques and data breaches could expose your unique biometric identifiers.
- Decentralized Technologies & Privacy: Blockchain, decentralized social media platforms, and other decentralized technologies have the potential to enhance privacy, but also create new attack vectors and privacy challenges if not implemented securely.
II. Proactive Strategies for Online Privacy in 2025:
-
Strengthening Authentication & Access Control:
- Multi-Factor Authentication (MFA) is Non-Negotiable: Use MFA for all online accounts, including hardware security keys (like YubiKey) for the highest level of security.
- Password Hygiene 2.0: Utilize strong, unique passwords for each account, generated and stored securely by a password manager. Consider passwordless authentication methods like passkeys, which are more resistant to phishing.
- Biometric Security with Cautions: Use biometric authentication with awareness of its potential vulnerabilities. Understand the privacy policies surrounding biometric data and choose reputable providers. Consider using biometric methods as a second factor of authentication, rather than as the primary method.
- Zero Trust Architecture: Implement a “zero trust” security model, where no user or device is implicitly trusted. This means verifying every access attempt, regardless of location or previous authentication.
-
Data Minimization & Privacy Awareness:
- Be a Data Minimalist: Limit the amount of personal information you share online. Think critically before providing personal data to any website or service.
- Privacy-Focused Search Engines: Utilize privacy-focused search engines like DuckDuckGo, which don’t track your search history.
- Review Privacy Policies Regularly: Take the time to read and understand the privacy policies of websites and services you use. Pay attention to how your data is collected, used, and shared. Look for data minimization practices.
- Control Your Social Media Footprint: Regularly review and adjust your social media privacy settings. Consider using tools to remove old posts or limit access to your past content. Use pseudonyms or alternative accounts for sensitive activities.
-
Secure Communication & Browsing:
- End-to-End Encrypted Messaging: Use end-to-end encrypted messaging apps like Signal for all sensitive communication.
- Virtual Private Networks (VPNs): Use a reputable VPN to encrypt your internet traffic and mask your IP address, especially when using public Wi-Fi. However, be aware that VPN providers themselves can be a point of vulnerability; choose carefully.
- Privacy-Focused Browsers and Extensions: Utilize privacy-focused browsers like Brave or Firefox with privacy-enhancing extensions (like Privacy Badger, uBlock Origin, and HTTPS Everywhere) to block trackers, ads, and other privacy-invading elements.
- Tor Browser: For maximum anonymity, consider using the Tor Browser, which routes your traffic through a network of relays to hide your location and browsing activity.
-
Defending Against AI-Powered Attacks:
- Skepticism and Critical Thinking: Be highly skeptical of any unsolicited communication or requests, especially those that seem urgent or too good to be true. Develop strong critical thinking skills to identify phishing attempts and deepfakes.
- Verify Information Independently: Don’t trust information you encounter online blindly. Verify the source and context of any information, especially financial requests.
- Voice and Video Verification: Be wary of voice or video calls from people you know or companies you trust. If possible, use a trusted alternative channel (e.g., a phone call on a secure line) to verify the identity of the caller.
- Security Awareness Training: Participate in regular security awareness training to learn about the latest phishing techniques, social engineering tactics, and other cyber threats.
-
Protecting Against Data Breaches & Surveillance:
- Data Breach Monitoring Services: Subscribe to data breach monitoring services that alert you if your personal information appears in a data breach.
- Privacy-Focused Mobile Devices & Operating Systems: Consider using smartphones and operating systems (like GrapheneOS or CalyxOS) designed with a focus on privacy and security. Alternatively, choose phones with strong security track records and update them frequently.
- Hardened Smart Device Configuration: Secure your smart home devices by using strong passwords, disabling unnecessary features, and keeping the firmware up to date. Create separate networks for IoT devices to isolate them from your primary network.
- Consider Privacy-Enhancing Technologies: Explore privacy-enhancing technologies such as homomorphic encryption, differential privacy, and secure multi-party computation, which are being developed to protect data in the cloud and other environments. These are likely to become more widespread in 2025.
- Advocate for Stronger Data Privacy Regulations: Support and advocate for stronger data privacy regulations, such as GDPR or CCPA, that limit data collection, require data minimization, and give individuals control over their personal information.
-
Preparing for Quantum Computing:
- Stay Informed: Keep abreast of developments in post-quantum cryptography.
- Prioritize Encryption Key Management: Ensure your encryption keys are securely stored and managed.
- Prepare for Upgrade Cycles: Be prepared for updates to your software and hardware to adopt post-quantum cryptographic algorithms.
III. Advanced Strategies and Tools:
- Self-Sovereign Identity (SSI): Explore SSI solutions, which allow you to control your digital identity and share only the necessary information for each interaction. This involves using decentralized identifiers (DIDs) and verifiable credentials (VCs).
- Privacy-Enhancing Technologies (PETs): Familiarize yourself with emerging PETs like zero-knowledge proofs, which allow you to prove something is true without revealing the underlying data.
- De-Googling & De-Apple-ing: Consider reducing your reliance on Google and Apple services, which collect vast amounts of data. Explore alternatives like ProtonMail, Nextcloud, and open-source operating systems.
- Personal Data Vaults: Consider using personal data vaults or secure data storage solutions to store your sensitive information in an encrypted and protected environment.
- Off-Grid Living & Physical Security: For the most sensitive information and to reduce your digital footprint, consider offline storage, “air-gapped” computers, and strong physical security measures.
IV. The Future of Privacy:
- The Privacy Arms Race: The battle for privacy will continue to escalate. As technology advances, so will the methods of surveillance and data collection.
- Data Ownership and Control: Individuals will demand more control over their personal data and how it is used. Regulations and technological solutions will likely evolve to address this demand.
- The Importance of Education and Awareness: Privacy education will be crucial. Individuals will need to be informed about the latest threats and best practices for protecting their personal information.
- Collaboration is Key: Governments, companies, and individuals will need to collaborate to create a more secure and private digital environment.
Conclusion:
Protecting your personal information online in 2025 will be a complex and dynamic undertaking. It requires a combination of technical skills, privacy awareness, proactive strategies, and continuous learning. By staying informed about the evolving threats and adopting a multi-layered approach to security, you can significantly reduce your risk and protect your personal information in the future. The future of privacy is not just about technology; it is about individual empowerment, ethical considerations, and the collective responsibility to safeguard our digital lives.