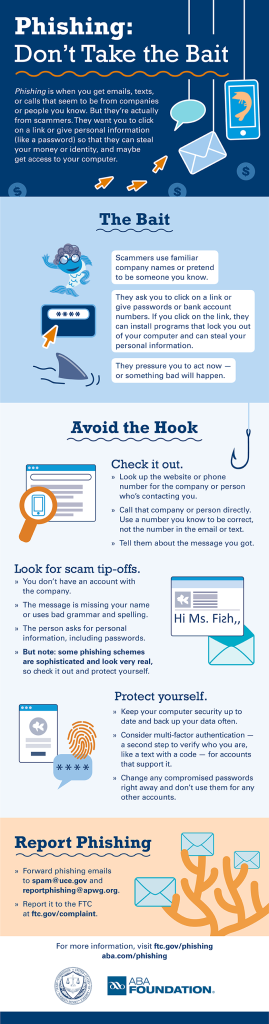
Don’t Get Hooked! A Deep Dive into Phishing and How to Outsmart the Scammers
Phishing. It’s a word that sounds like something you do with a rod and a worm, but instead of reeling in a tasty fish, you’re potentially reeling in disaster. In today’s digital age, where our lives are increasingly intertwined with the internet, understanding and avoiding phishing scams is more critical than ever. These deceptive schemes are constantly evolving, becoming more sophisticated and harder to spot. Let’s equip you with the knowledge to recognize and avoid these digital traps, so you can navigate the online world safely.
Understanding the Bait: What Exactly is Phishing?
Phishing, at its core, is a form of cybercrime where attackers try to trick you into giving them sensitive information. Think of it like a digital con artist sending out carefully crafted lures, hoping to snag your username, password, credit card details, or other personal data. These attacks often arrive in the form of seemingly legitimate emails, text messages, or even phone calls.
They’re masters of disguise, impersonating trusted entities like banks, social media platforms, government agencies, or even your favorite online retailers. Their ultimate goal? To steal your data and potentially use it for financial gain or identity theft.
The Digital Fishing Line: Common Phishing Tactics
Phishers aren’t just sending out random emails; they’re employing clever tactics to maximize their chances of success. Here are some of the most common lures you need to be aware of:
1. The Urgent Appeal:
These messages create a sense of urgency, pressuring you to act immediately. They might claim your account has been compromised, a payment is overdue, or you’ve won a prize (too good to be true, right?). The goal is to bypass your critical thinking and get you to click a malicious link or provide sensitive information before you have a chance to fully assess the situation.
2. The “Too Good to be True” Offer:
Free iPads! Massive discounts! Unbelievable deals! If something sounds too good to be true, it probably is. Phishers often use these enticing offers to lure you into clicking on links or providing your details, promising rewards that never materialize.
3. The Impersonation Game:
Phishers are excellent impersonators. They’ll often mimic the branding, logos, and even the email format of legitimate companies to trick you into believing their messages are authentic. Be extra vigilant if an email from your bank suddenly looks different from what you’re used to.
4. The Suspicious Link:
This is the primary weapon of choice. The email or message will contain a link that looks legitimate at first glance, but in reality, leads to a fake website designed to steal your information. Often, the link will redirect to a website that looks almost identical to the real one, making it even harder to detect.
5. The Attached Malware:
While less common than links, some phishing emails contain malicious attachments like PDF files, Word documents, or Excel spreadsheets. These attachments can contain malware that, once opened, infects your device and steals your data.
Red Flags: Spotting the Phish
Even the most sophisticated phishing attempts leave clues. Here’s a table of red flags you should be on the lookout for:
| Red Flag | Description |
|---|---|
| Suspicious Sender Address | Unusual email address, mismatched domain name, or generic greeting |
| Poor Grammar and Spelling | Typos, grammatical errors, and unprofessional language |
| Urgent Tone | Demands immediate action or threatens negative consequences |
| Requests for Personal Info | Asks for sensitive data like passwords, credit card details |
| Suspicious Links/Attachments | Hover over links to check destination; avoid opening attachments from unknown senders |
| Inconsistent Branding | Differences in logo, colors, or overall design |
| Generic Greetings | “Dear Customer” or “Dear User” instead of your name |
Casting Your Own Net: How to Protect Yourself
Now that you know how to identify the phish, let’s talk about how to protect yourself. Here’s a breakdown of proactive steps you can take:
1. Be Skeptical:
The most crucial defense is a healthy dose of skepticism. Assume every unsolicited email or message could be a phishing attempt, especially if it involves any of the red flags listed above.
2. Verify, Verify, Verify:
If you receive a suspicious message, don’t click on any links or open any attachments. Instead, go directly to the company’s official website or call their customer service number to verify the message’s authenticity.
3. Hover Before You Click:
Before clicking on a link, hover your mouse over it to see the actual URL. Does it match the website it claims to be? If it looks suspicious, don’t click it.
4. Strong Passwords and Two-Factor Authentication (2FA):
Use strong, unique passwords for all your online accounts. Consider using a password manager to generate and store them securely. Enable two-factor authentication (2FA) wherever possible. This adds an extra layer of security by requiring a code from your phone in addition to your password.
5. Keep Your Software Updated:
Regularly update your operating system, web browser, and security software. These updates often include security patches that protect you from known vulnerabilities that phishers can exploit.
6. Be Careful with Public Wi-Fi:
Avoid entering sensitive information when connected to public Wi-Fi networks, as they can be less secure. Consider using a VPN (Virtual Private Network) to encrypt your internet traffic and protect your data.
7. Educate Yourself and Others:
Stay informed about the latest phishing tactics and share your knowledge with family and friends. The more people are aware of these scams, the safer everyone will be.
8. Report Phishing Attempts:
Report any phishing attempts you encounter to the relevant authorities or organizations, such as your bank, the Federal Trade Commission (FTC), or the Anti-Phishing Working Group (APWG). This helps to alert others and prevent future scams.
Actionable Checklist: Your Phishing Defense
Here’s a simple checklist to follow:
- Think before you click.
- Verify the source of emails and links.
- Use strong passwords and 2FA.
- Keep your software updated.
- Report suspicious activity.
The Fight Continues: Staying Vigilant
Phishing is a constant battle. The techniques used by attackers will continue to evolve, so it’s essential to stay vigilant and informed. By understanding the tactics, recognizing the red flags, and following these preventative measures, you can significantly reduce your risk of falling victim to a phishing scam. Stay sharp, stay safe, and don’t let the phishers reel you in!

Additional Information
Recognizing and Avoiding Phishing Scams: A Deep Dive
Phishing scams are a persistent and evolving threat that can trick even the most tech-savvy individuals. They leverage deception and urgency to steal sensitive information like usernames, passwords, credit card details, and personal data. This detailed analysis will provide you with the knowledge and tools to recognize and avoid these scams.
I. Understanding Phishing: The Core Concepts
-
What is Phishing? Phishing is a type of cybercrime where attackers impersonate a legitimate entity (bank, social media platform, government agency, etc.) to deceive victims into divulging personal information. The goal is often financial gain, identity theft, or installing malware.
-
Key Characteristics of Phishing Attacks:
- Deception and Impersonation: Scammers craft messages that mimic the branding, language, and design of legitimate organizations.
- Urgency and Fear: Phishing emails often create a sense of urgency or threat (e.g., “Your account has been compromised,” “You must update your information immediately”) to pressure victims into acting quickly without thinking.
- Lure of Rewards or Threats: Phishing attempts may promise rewards (e.g., “Claim your free gift card!”) or threaten negative consequences (e.g., “Your account will be suspended”).
- Use of Links and Attachments: Phishing relies heavily on malicious links that lead to fake websites designed to steal information or download malware. They also use infected attachments (e.g., PDF, Word documents) that contain malware.
- Mass Distribution or Spear Phishing: Phishing attacks can be broad (targeting many users) or highly targeted (spear phishing, often aimed at specific individuals or organizations with more tailored messages based on research of the victim).
- Evolving Tactics: Scammers constantly adapt their techniques to stay ahead of security measures. This includes using more sophisticated language, mimicking legitimate websites with greater accuracy, and leveraging new technologies.
II. Recognizing Phishing Attempts: Red Flags to Watch Out For
-
Suspicious Sender Information:
- Unfamiliar Email Address: The email address might be slightly off, using a domain name that’s close but not quite right (e.g., “amaz0n.com” instead of “amazon.com”).
- Generic Greetings: Instead of using your name (e.g., “Dear John Smith”), the email might use generic greetings like “Dear Customer” or “Dear User.”
- Domain Name Mismatch: The sender’s display name might appear legitimate, but the actual email address doesn’t match the purported sender’s organization (e.g., an email from “Chase Bank” using a Gmail address).
- Unsolicited Emails: Be wary of unexpected emails, especially those requesting personal information. If you didn’t request the communication, it should be treated with caution.
- Unusual Sending Times: Emails arriving at odd hours or with unexpected timing could be a sign of phishing, especially if they require immediate action.
-
Suspicious Content:
- Poor Grammar and Spelling: Phishing emails often contain grammatical errors, spelling mistakes, and awkward phrasing.
- Unnatural Tone or Language: The language might sound overly formal, overly friendly, or inconsistent with the typical communications of the purported sender.
- Requests for Personal Information: Legitimate organizations rarely ask for sensitive information (passwords, credit card numbers, social security numbers) via email.
- Threatening Language or Pressure Tactics: Be wary of emails that threaten to close your account, charge fees, or take other actions if you don’t respond immediately.
- Urgent or Impulsive Language: Phishing scams are often designed to provoke an emotional response and bypass rational thinking. Phrases like “Act now!”, “Limited time offer!”, “Immediate action required!” are red flags.
- Inconsistent Information: Compare the information in the email with what you know. Does it align with your existing account details or recent interactions with the organization? If the information doesn’t line up, this raises suspicion.
- Generic Information: A lack of personalization or specific information about your account or past interactions can indicate a generic phishing attempt.
- Suspicious Attachments: Be cautious about opening attachments from unknown senders or those you weren’t expecting. They could contain malware. Even attachments from known senders should be treated with suspicion if you weren’t expecting one.
-
Suspicious Links and Websites:
- Hover Before Clicking: Before clicking on any link in an email, hover your mouse over it (without clicking). This will reveal the actual URL. If the URL doesn’t match the purported sender’s website, it’s likely a phishing link. Look for subtle discrepancies like extra characters, misspellings, or unfamiliar domain names.
- Shortened URLs: Be extra cautious about links shortened using URL shorteners like Bitly or TinyURL. These can hide the true destination of the link, making it harder to verify.
- Look for Security Indicators: When you do click on a link, check the URL in your browser’s address bar.
- HTTPS: Look for “HTTPS” at the beginning of the URL (the “S” stands for “secure”). This indicates that the website uses encryption to protect your data.
- Lock Icon: A locked padlock icon next to the URL also indicates a secure connection.
- Domain Accuracy: Ensure the domain name is correct (e.g., “amazon.com”). Scammers often use similar-looking domain names to deceive users (e.g., “amaz0n.com”).
- Unfamiliar Website Design: Compare the website to the legitimate website. Phishing sites may look visually similar, but there might be subtle differences in the layout, logo, or overall design. Also, look for poor design, broken links, or a lack of standard features.
- Requests for Personal Information on Unusual Pages: Even on a secure website, be skeptical if a legitimate website asks for personal information on an unusual page. Go to the website through your browser’s address bar or a saved bookmark.
- Suspicious Pop-ups: Be wary of unexpected pop-ups that ask for information, especially on websites you don’t trust.
- Suspicious Redirects: If you’re redirected to a different website than expected, this could be a phishing attempt.
III. Avoiding Phishing Scams: Best Practices for Protection
- Think Before You Click: This is the most crucial advice. Always question the legitimacy of an email before clicking on any links or opening any attachments.
- Verify Information Independently: If you’re unsure about an email’s legitimacy, don’t click on any links. Instead, go to the organization’s official website directly (by typing the address into your browser or using a saved bookmark) or contact them through a known phone number to verify the information.
- Never Give Out Personal Information: Never provide sensitive information (passwords, credit card numbers, social security numbers, etc.) via email or on websites you’re unsure about. Legitimate organizations will not typically ask for such information via email.
- Use Strong, Unique Passwords: Create strong, unique passwords for all your online accounts and avoid reusing passwords. Use a password manager to help generate and store complex passwords securely.
- Enable Two-Factor Authentication (2FA): Enable 2FA (also known as multi-factor authentication) on all accounts that offer it. This adds an extra layer of security by requiring a verification code from a trusted device (e.g., your phone) in addition to your password.
- Keep Your Software Updated: Regularly update your operating system, web browser, and other software applications. Updates often include security patches that protect against known vulnerabilities.
- Use a Reputable Antivirus/Antimalware Program: Install and regularly update a reputable antivirus/antimalware program. These programs can help detect and block phishing attempts and malware infections.
- Be Careful with Public Wi-Fi: Avoid entering sensitive information on public Wi-Fi networks. Use a Virtual Private Network (VPN) to encrypt your internet traffic when using public Wi-Fi.
- Educate Yourself and Others: Stay informed about the latest phishing scams and share your knowledge with friends, family, and colleagues. Phishing is a constantly evolving threat, so continuous learning is crucial.
- Report Phishing Attempts: Report any suspected phishing emails or websites to the organization being impersonated and to your email provider (e.g., Gmail, Outlook). This helps them take action to protect other users. You can also report phishing attempts to the Federal Trade Commission (FTC).
- Be Wary of Social Media Scams: Be cautious of links and messages on social media platforms. Scammers use social media to spread phishing campaigns and target users with targeted messages.
- Be Careful of Phone Calls and Texts (Smishing and Vishing): Phishing attempts aren’t limited to email. Be wary of unsolicited phone calls (vishing) and text messages (smishing) that request personal information.
IV. Specific Phishing Techniques and Examples:
- Spear Phishing: Highly targeted attacks aimed at specific individuals or organizations. Scammers research their victims and tailor messages to make them appear more credible. They might use information gathered from social media, professional networking sites, or public records.
- Example: An email to a company’s CFO, purportedly from the CEO, asking for a wire transfer to a specific account, making the transaction sound urgent.
- Whaling: A specific type of spear phishing targeting high-level executives or other high-profile individuals.
- Example: An email impersonating a lawyer or a regulator threatening legal action if the executive doesn’t provide financial information.
- Business Email Compromise (BEC): A sophisticated form of phishing where attackers gain access to a business email account and then use it to impersonate an employee, often targeting financial departments or vendors to request fraudulent payments.
- Example: A scammer gains access to a CFO’s email and then sends an email to the accounts payable department requesting a change in payment details for a regular vendor.
- Smishing (SMS Phishing): Phishing attempts conducted via text message. Scammers often send text messages with links to fake websites or ask for sensitive information.
- Example: A text message claiming to be from your bank, stating that your account has been locked and requesting you to click a link to unlock it.
- Vishing (Voice Phishing): Phishing attempts conducted via phone calls. Scammers often impersonate government agencies, banks, or other organizations and try to obtain personal information over the phone.
- Example: A phone call claiming to be from the IRS, threatening legal action unless you immediately pay back taxes.
- QR Code Phishing: Phishing using malicious QR codes. When scanned, these codes can direct users to phishing websites or download malware.
- Example: A QR code on a flyer promising a discount, but when scanned, takes the user to a fake login page for a popular retailer.
V. What to Do If You Suspect You’ve Been Phished:
- Stop Responding: Do not reply to the email, click on any links, or open any attachments.
- Change Your Passwords: Immediately change your passwords for any accounts you suspect may have been compromised, especially banking, email, and social media accounts.
- Monitor Your Accounts: Regularly monitor your bank accounts, credit card statements, and other online accounts for any unauthorized activity.
- Contact the Organization Being Impersonated: Report the phishing attempt to the organization whose brand was used in the scam (e.g., your bank, social media platform).
- Run a Malware Scan: Run a full scan of your computer using a reputable antivirus/antimalware program.
- Report the Incident: Report the phishing attempt to the FTC (www.ftc.gov) and your local law enforcement agency.
- Consider Identity Theft Protection: If you believe your identity has been stolen, consider signing up for identity theft protection services that can monitor your credit reports and other personal information.
- Lock or Freeze Your Credit: If you suspect financial information has been compromised, consider placing a fraud alert or credit freeze on your credit reports.
VI. The Evolving Threat Landscape and Future Trends
- AI-Powered Phishing: Artificial intelligence is being used to create increasingly sophisticated and personalized phishing attacks. AI can generate more convincing content, mimic user behavior, and even adapt in real-time to evade detection.
- Deepfakes and Synthetic Identities: Scammers are using deepfake technology to create realistic videos and audio recordings of individuals, making it harder to verify the authenticity of communications. Synthetic identities (fake online profiles) can also be used to launch phishing campaigns and build trust.
- Phishing as a Service (PaaS): Phishing tools and services are increasingly available for purchase on the dark web, making it easier for less tech-savvy individuals to launch phishing attacks.
- Mobile-First Phishing: As mobile devices become more prevalent, attackers are shifting their focus to mobile phishing tactics, such as smishing, malicious mobile apps, and fake mobile websites.
- Social Engineering: Phishing is just one component of a broader attack strategy known as social engineering, which involves manipulating people into divulging confidential information or performing actions that compromise security. Attackers are becoming more adept at using psychological techniques and leveraging social media to target their victims.
VII. Conclusion
Recognizing and avoiding phishing scams requires vigilance, critical thinking, and a proactive approach to cybersecurity. By understanding the tactics used by scammers, knowing the red flags to watch out for, and practicing safe online habits, you can significantly reduce your risk of becoming a victim. Stay informed about the latest phishing trends and adapt your security practices accordingly. Remember, the best defense against phishing is to be skeptical and to verify everything. By taking these precautions, you can protect your personal information, financial assets, and online reputation.