The Unseen Shield: Why Regular Software Updates Are Your Cybersecurity Superpower
Imagine your computer, your phone, your entire digital life as a magnificent castle. You’ve got drawbridges, moats, and guards (your antivirus software, firewalls, and password practices). But castles, no matter how impressive, are vulnerable. Tiny cracks can appear in the walls, hidden tunnels might be dug, and clever enemies can exploit weaknesses you never even knew existed. This is where software updates step in – the vigilant repair crew, tirelessly patching vulnerabilities and fortifying your digital fortress.
The Patchwork of Protection: Understanding Software Updates
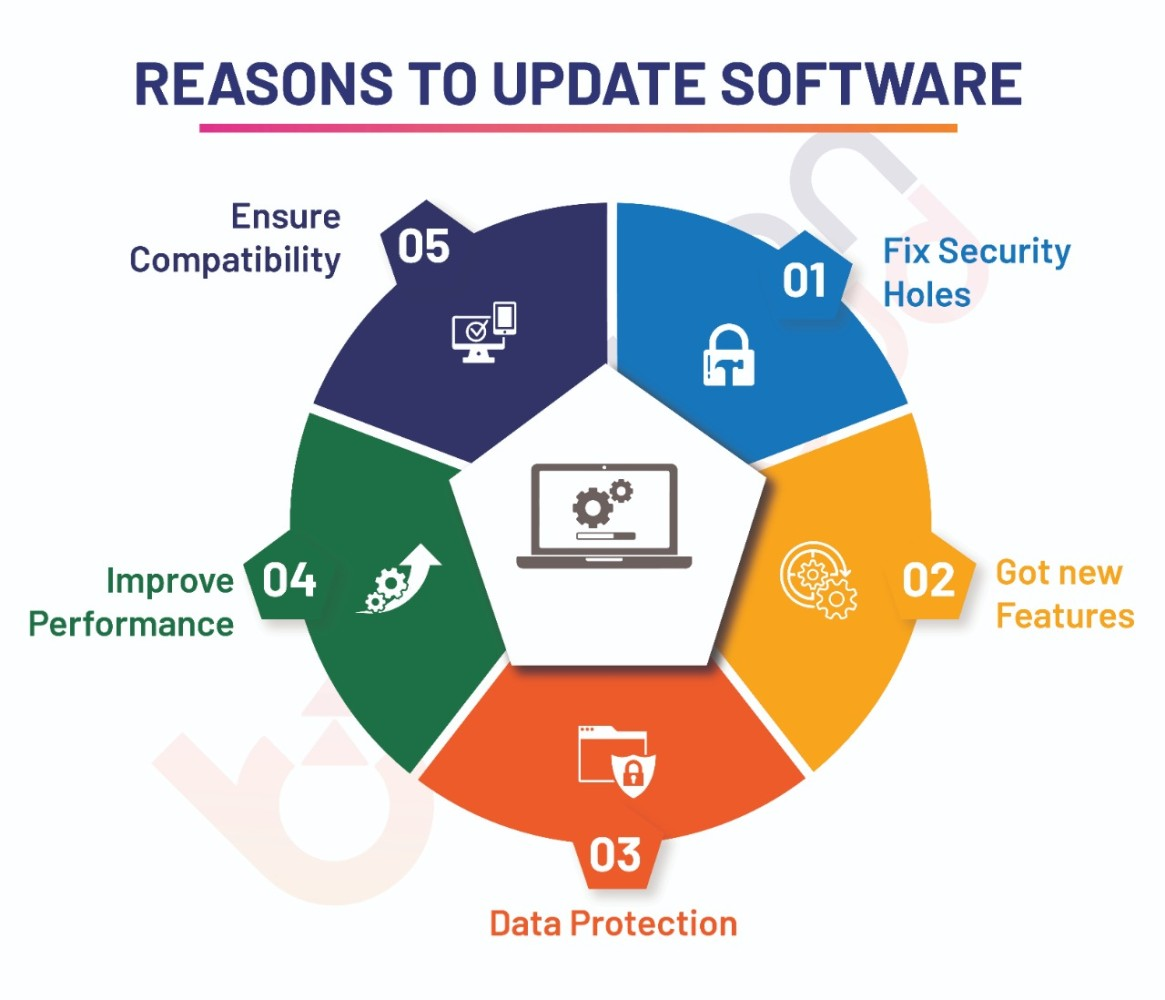
Software updates aren’t just about getting the latest emoji or a slightly sleeker interface. They’re about security. They’re about fixing the bugs – the flaws in the code – that cybercriminals exploit. These updates come in various forms:
-
Security Updates: These are the heavy hitters. They address known vulnerabilities that could be used to compromise your system. Think of them as patching up gaping holes in your castle walls.
-
Bug Fixes: Even software that’s seemingly perfect often has minor glitches. These updates squash those bugs, improving performance and stability, but they can indirectly enhance security by removing unexpected attack vectors. They are the maintenance crew, keeping the castle running smoothly.
-
Feature Updates: These introduce new functionality. While not directly security-focused, they can sometimes include underlying improvements to the system that inadvertently enhance security. They are the architects, constantly designing and building stronger fortifications.
The Cybercriminal’s Handbook: How Exploits Work
Cybercriminals are constantly scanning for weaknesses. They’re like treasure hunters, searching for the unguarded entrance to your digital vault. They use:
-
Known Vulnerabilities (Zero-Days are a different threat!): These are weaknesses in software that developers are aware of and working to fix, but haven’t yet been patched. Think of a faulty door hinge that everyone knows about but hasn’t been fixed yet. Attackers often race to exploit these vulnerabilities before updates are released.
-
Malware: Malicious software, designed to damage or gain access to a computer system. Software updates often include improved defenses against known malware strains. They are the updated traps and security patrols, constantly learning to identify and eliminate threats.
-
Phishing & Social Engineering: Tricking users into revealing sensitive information like passwords or credit card numbers. While updates can’t directly prevent phishing, they can improve the security of your email clients and browsers, making it harder for attackers to succeed. These attackers are the deceitful strangers trying to persuade the castle inhabitants to open the gates.
The Cost of Complacency: Why Ignoring Updates is a Risk
Ignoring updates is like ignoring a leak in your roof. It might seem harmless at first, but the longer you wait, the more damage is likely to occur. The consequences can be severe:
| RISK | DESCRIPTION |
|---|---|
| Data Breaches | Sensitive information (passwords, financial data, personal details) stolen. |
| Malware Infections | Viruses, ransomware, and other malicious software that can cripple your system. |
| System Downtime | Your devices become unusable, causing disruption and lost productivity. |
| Reputational Damage | If your company’s systems are compromised, it can damage trust with customers and partners. |
| Financial Loss | Costs associated with data recovery, incident response, legal fees, and potential fines. |
| Identity Theft | Cybercriminals stealing personally identifiable information to commit identity fraud. |
| Loss of Control | Attackers taking over your system for their own malicious purposes. |
The Update Ritual: Best Practices for Cybersecurity
Making software updates a regular part of your routine is crucial. Here’s how to do it right:
-
Enable Automatic Updates: Most operating systems and applications allow you to automate the update process. This is the easiest and most effective way to stay protected.
-
Check Regularly: Even with automatic updates, it’s wise to occasionally check manually, especially for critical software like your operating system, web browser, and antivirus software.
-
Update Immediately When Possible: Don’t delay applying updates. The sooner you patch vulnerabilities, the less time attackers have to exploit them.
-
Update All Devices: This includes your computer, smartphone, tablet, router, smart home devices, and any other connected gadgets.
-
Stay Informed: Follow reputable cybersecurity blogs and news sources to learn about new vulnerabilities and the latest threats.
-
Practice Good Password Hygiene: Use strong, unique passwords for all your accounts.
-
Use Antivirus Software: Keep your antivirus software updated and running in the background.
Conclusion: Your Digital Duty
Regular software updates are not just a technical chore; they are a fundamental pillar of cybersecurity. They are the invisible armor that protects you, your data, and your privacy. By embracing the update ritual, you are proactively building a safer, more resilient digital future, ensuring your digital castle remains strong and secure against the ever-evolving threats of the online world. Embrace the power of the update, and become your own cybersecurity champion.
Additional Information
The Importance of Regular Software Updates in Cybersecurity: A Deep Dive
Regular software updates are not just a convenience; they are a cornerstone of modern cybersecurity. They act as the primary line of defense against a constantly evolving threat landscape, shielding systems and data from vulnerabilities that attackers actively exploit. Here’s a detailed analysis of their importance:
1. Vulnerability Remediation & Patching:
- The Problem: Software is inherently complex. Development processes can introduce bugs and security flaws (vulnerabilities). These vulnerabilities can range from simple coding errors to serious design flaws that can be exploited by malicious actors.
- The Solution: Software updates frequently include “patches” – code designed to fix these vulnerabilities. These patches are the primary mechanism for closing security holes and preventing attackers from gaining access to systems or data.
- Detailed Analysis:
- Zero-Day Exploits: These are vulnerabilities that are known to attackers but not yet known to software vendors, leaving systems completely exposed. While updates can’t prevent them directly, rapid patching after a zero-day is discovered is crucial to minimize damage.
- Public Disclosure: Once a vulnerability is identified and disclosed (e.g., through security advisories or research), attackers quickly develop exploits to leverage it. The longer systems remain unpatched, the higher the risk of compromise.
- Automated Exploitation: Attackers automate the process of scanning networks for vulnerable systems. Unpatched systems are easily identified and targeted, making them low-hanging fruit for attackers.
- Patch Testing & Rollout: Vendors often test patches extensively before release to ensure they don’t introduce new problems. However, organizations should also test patches in a non-production environment before widespread deployment to avoid potential conflicts or system instability.
2. Protection Against Malware and Exploits:
- The Problem: Attackers constantly develop new malware and exploit techniques to bypass existing security measures. This includes:
- Ransomware: Encrypting user data and demanding payment for its release.
- Spyware: Stealing sensitive information, such as passwords and financial data.
- Trojans: Disguising malicious code as legitimate software to gain unauthorized access.
- Rootkits: Concealing malicious activity and providing persistent access to a system.
- The Solution: Updates often include:
- Signature Updates: Updated definitions that identify and block new malware strains based on their unique characteristics.
- Improved Detection Mechanisms: Enhanced anti-malware engines that use sophisticated techniques (e.g., behavioral analysis, heuristic analysis) to detect and block evolving threats.
- Security Feature Enhancements: Improvements to operating systems, applications, and firewalls that make it more difficult for attackers to exploit known vulnerabilities.
- Detailed Analysis:
- Defense in Depth: Software updates are just one component of a comprehensive security strategy, but a crucial one. Combining updates with other security controls (firewalls, intrusion detection systems, user awareness training) creates a layered defense.
- Endpoint Protection: Regularly updating endpoint security software (antivirus, anti-malware, endpoint detection and response – EDR) is critical to protect individual devices and prevent malware infections from spreading within a network.
- Software Composition Analysis (SCA): Tools that analyze a software application’s components (libraries, dependencies) to identify known vulnerabilities can aid in prioritizing updates and remediation efforts.
3. Data Integrity & Confidentiality:
- The Problem: Vulnerabilities can lead to data breaches, where sensitive information is stolen or exposed. This can result in financial losses, reputational damage, legal penalties, and loss of customer trust.
- The Solution: Updates can improve the integrity and confidentiality of data by:
- Fixing Authentication and Authorization Flaws: Preventing unauthorized access to data by strengthening user authentication mechanisms and enforcing proper access controls.
- Protecting Against Injection Attacks (e.g., SQL Injection): Preventing attackers from injecting malicious code into applications or databases to steal, modify, or delete data.
- Enhancing Encryption Protocols: Strengthening encryption algorithms and protocols used to protect data in transit and at rest.
- Detailed Analysis:
- Compliance Requirements: Many industry regulations (e.g., HIPAA, GDPR, PCI DSS) mandate regular software updates to protect sensitive data. Failing to comply can result in significant fines and legal consequences.
- Incident Response: Promptly applying updates after a data breach is essential to prevent further damage and to demonstrate a commitment to data security.
- Data Loss Prevention (DLP): While DLP tools can help prevent data leakage, regular software updates are vital to ensuring that underlying systems are secure and that DLP tools themselves are functioning effectively.
4. System Stability and Performance:
- The Problem: Bugs and errors in software can lead to system crashes, performance degradation, and other operational problems.
- The Solution: Updates often include bug fixes, performance optimizations, and improved stability.
- Detailed Analysis:
- Availability: Regular updates help to ensure that systems are available and functioning as intended, minimizing downtime and disruptions to business operations.
- User Experience: Performance improvements enhance the user experience, making systems more responsive and efficient.
- Security and Stability Intertwined: Sometimes, updates can introduce new vulnerabilities or cause unforeseen issues. Thorough testing and a robust update management process are essential to balance security and stability.
5. Regulatory Compliance:
- The Problem: Many industries are subject to regulations that require organizations to maintain secure systems and protect sensitive data.
- The Solution: Regular software updates are often a key requirement for compliance with these regulations.
- Detailed Analysis:
- Industry-Specific Standards: Different industries (e.g., finance, healthcare, government) have specific compliance requirements that mandate the patching of vulnerabilities and the implementation of security controls.
- Audits and Assessments: Organizations are often subject to audits and security assessments to ensure that they are meeting compliance requirements. Documentation of the update process and adherence to patch management policies is crucial for demonstrating compliance.
- Data Privacy Laws: Data privacy regulations (e.g., GDPR, CCPA) require organizations to protect personal data. Software updates help to meet these obligations by addressing vulnerabilities that could lead to data breaches.
Challenges of Implementing Regular Software Updates:
- Compatibility Issues: Updates can sometimes cause compatibility issues with other software or hardware, requiring careful testing and planning before deployment.
- Downtime: Installing updates may require system downtime, which can disrupt business operations.
- Resource Constraints: Organizations may lack the resources (staff, budget, time) to manage the update process effectively.
- Complexity: Managing updates across a large and diverse IT infrastructure can be complex.
- False Positives: Sometimes, updates intended to fix security issues can introduce new vulnerabilities or disrupt system operations. Thorough testing is crucial to identify and address these issues.
Best Practices for Implementing a Robust Update Management Program:
- Develop a Patch Management Policy: Define a clear policy that outlines the organization’s approach to updating software. This should include:
- Scope: Which systems and software are included in the update program.
- Prioritization: How vulnerabilities are prioritized based on severity and risk.
- Testing: Procedures for testing updates before deployment.
- Deployment: The process for deploying updates, including scheduling and automation.
- Reporting: How update status and compliance are tracked.
- Vendor Coordination: Working with software vendors to receive timely notifications about new updates and security advisories.
- Automate the Update Process: Use patch management tools to automate the process of identifying, downloading, testing, and deploying updates.
- Prioritize Updates Based on Risk: Focus on patching critical vulnerabilities (those with a high CVSS score, or those being actively exploited) first.
- Test Updates Thoroughly: Test updates in a non-production environment before deploying them to production systems.
- Monitor and Report on Update Status: Track the status of updates and generate reports to demonstrate compliance.
- Maintain a Backup and Disaster Recovery Plan: Have a plan in place to restore systems from backups if an update causes problems.
- Train Employees: Educate employees about the importance of software updates and how to identify and report potential security issues.
- Stay Informed: Keep up-to-date on the latest security threats and vulnerabilities, and adjust the update strategy accordingly. Subscribe to security advisories and vendor newsletters.
Conclusion:
Regular software updates are not optional in the current threat landscape; they are essential for maintaining a robust cybersecurity posture. By diligently implementing a comprehensive update management program that prioritizes patching vulnerabilities, protecting against malware, ensuring data integrity, and meeting compliance requirements, organizations can significantly reduce their risk of cyberattacks and protect their valuable assets. Ignoring the importance of regular updates is akin to leaving the front door of your house wide open to intruders. It’s a fundamental security practice that must be prioritized to safeguard systems, data, and business continuity.





