The Rise of Ransomware: How to Defend Against This Growing Threat
(Keywords: ransomware, cybersecurity, data breaches, cyberattacks, malware, data protection, incident response, endpoint security, threat intelligence, phishing, backups, security awareness)
The digital age has woven itself into the very fabric of our lives, connecting us in unprecedented ways. But this interconnectedness has also spawned a shadowy adversary: ransomware. This isn’t just a tech problem; it’s a human problem, impacting businesses, governments, and individuals alike. It’s a digital mugging, a virtual extortion scheme, and the rise of ransomware demands a strategic, evolving defense.
The Anatomy of a Digital Hostage: Understanding the Ransomware Threat
Ransomware, at its core, is malicious software (malware) that encrypts a victim’s data and demands a ransom payment, often in cryptocurrency, for its decryption. The sophistication and distribution methods of ransomware have dramatically increased, making it a persistent and pervasive threat. Gone are the days of simplistic attacks; today’s ransomware is complex, targeted, and devastating.
Key Stages of a Ransomware Attack:
- Infection Vector: How the ransomware gains initial access.
- Payload Delivery: The execution of the ransomware on the compromised system.
- Encryption: Data is encrypted using a strong encryption algorithm.
- Ransom Demand: The victim receives instructions and a demand for payment.
- Payment & Decryption (Hopefully): The victim pays, and in some cases, receives a decryption key.
From Simple Scams to Sophisticated Syndicates: The Evolution of Ransomware
The early iterations of ransomware were clumsy and easily thwarted. But over time, the criminals behind these attacks have refined their tactics, adopted more sophisticated techniques, and formed organized criminal syndicates. These criminal organizations operate with alarming efficiency, creating a thriving, lucrative ecosystem.
Ransomware Evolution Timeline (Simplified):
| Phase | Characteristics | Impact |
|---|---|---|
| Early Scareware | Basic lockscreens, unsophisticated threats | Limited damage, easy removal |
| Crypto-Ransomware | Data encryption, ransom demands | Significant data loss, financial disruption |
| RaaS (Ransomware-as-a-Service) | Pre-packaged ransomware, affiliate programs | Mass attacks, accessibility to less skilled actors |
| Double Extortion | Data exfiltration + encryption | Increased leverage, higher ransom demands |
The rise of “Ransomware-as-a-Service” (RaaS) has democratized cybercrime, allowing even less tech-savvy individuals to launch attacks. This has led to a surge in the number of ransomware incidents and has made every organization a potential target. The more recent “double extortion” tactic, where criminals not only encrypt data but also steal it and threaten to release it publicly, has significantly increased the pressure on victims to pay the ransom.
Defense in Depth: Building a Robust Ransomware Defense Strategy
A single security measure is rarely enough. Building a robust defense against ransomware requires a multi-layered approach, encompassing technology, policies, and human awareness. This is a journey, not a destination, so continual monitoring, adaptation, and improvement are vital.
1. Endpoint Security: The First Line of Defense
Endpoint security solutions, like antivirus software and endpoint detection and response (EDR) tools, are crucial for preventing ransomware from reaching your systems in the first place.
Endpoint Security Must-Haves:
- Up-to-Date Antivirus Software: Crucial for detecting and blocking known malware.
- EDR (Endpoint Detection and Response): Provides real-time monitoring, threat hunting, and incident response capabilities.
- Application Control: Restricts the execution of unauthorized or untrusted applications.
- Regular Patching: Keep software updated to address known vulnerabilities.
2. Network Segmentation: Containing the Blast Radius
If ransomware does manage to penetrate your network, network segmentation limits the damage by isolating infected systems.
Network Segmentation Best Practices:
- Divide your network into smaller, isolated segments.
- Implement strict access controls to limit movement between segments.
- Use firewalls to control traffic flow.
- Monitor network traffic for suspicious activity.
3. Backup and Disaster Recovery: Your Insurance Policy
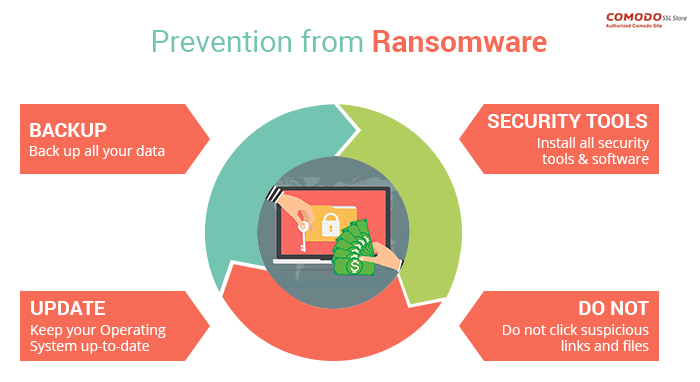
Regular, tested backups are your last line of defense. If you’re hit with ransomware, you can restore your data and avoid paying the ransom. Remember, paying the ransom doesn’t guarantee data recovery, and it encourages further criminal activity.
Backup Best Practices:
- Implement a robust and frequent backup schedule.
- Store backups offline and offsite.
- Test backups regularly to ensure data integrity.
- Practice data restoration procedures.
4. Security Awareness Training: Empowering Your Human Firewall
Humans are often the weakest link in cybersecurity. Phishing attacks, social engineering, and other human-based attacks are common ransomware infection vectors. Security awareness training helps your employees recognize and avoid these threats.
Key Security Awareness Training Topics:
- Phishing Awareness: Recognizing and reporting phishing emails.
- Password Security: Creating and managing strong passwords.
- Social Engineering Awareness: Identifying and avoiding social engineering tactics.
- Safe Browsing Practices: Avoiding malicious websites and downloads.
- Incident Reporting Procedures: Knowing how to report security incidents.
5. Incident Response Planning: Preparing for the Inevitable
A well-defined incident response plan is critical for minimizing damage and restoring operations quickly in the event of a ransomware attack. This plan should outline the steps to be taken, the roles and responsibilities of the individuals involved, and the communication protocols to be followed.
Key Components of an Incident Response Plan:
- Detection and Analysis: Identifying and assessing the attack.
- Containment: Preventing the spread of the infection.
- Eradication: Removing the ransomware and malicious software.
- Recovery: Restoring systems and data.
- Post-Incident Activity: Reviewing the incident and implementing improvements.
6. Threat Intelligence: Staying Ahead of the Curve
Threat intelligence provides valuable insights into current and emerging ransomware threats, allowing you to proactively defend your organization.
Sources of Threat Intelligence:
- Industry Reports: Reports from security vendors and research firms.
- Security News and Blogs: Stay informed about the latest ransomware trends.
- Threat Sharing Communities: Participate in or monitor threat sharing communities.
- Internal Monitoring: Analyze your own logs and security data.
Beyond the Basics: Advanced Ransomware Mitigation Techniques
Beyond the core defensive measures, there are more advanced techniques that can further strengthen your defenses.
1. Zero Trust Architecture
A zero-trust architecture assumes that no user or device, inside or outside the network, can be trusted by default. This approach requires strong authentication and authorization, and continuously monitors and validates users and devices before granting access to resources.
2. Deception Technology
Deception technology involves setting up decoy systems and data designed to lure attackers and reveal their presence. This can help detect ransomware attacks early and provide valuable information about attacker tactics.
3. Data Encryption and Access Controls
Encrypting sensitive data, both at rest and in transit, can limit the impact of a ransomware attack by making it harder for attackers to access valuable information even if they manage to encrypt the data. Implement strict access controls to ensure that users only have access to the data and systems they need to perform their job functions.
The Future of Ransomware Defense: Staying Ahead of the Curve
Ransomware is an ever-evolving threat. As the tactics and techniques of ransomware attackers change, so must our defenses. Future defense strategies will likely include:
- AI-powered security solutions: AI and machine learning will be used to automate threat detection, incident response, and vulnerability management.
- Automation: Automating security tasks, such as patching, configuration, and threat hunting, will improve efficiency and reduce the risk of human error.
- Collaboration and Information Sharing: Sharing threat intelligence and best practices across industries and organizations will be crucial for staying ahead of the attackers.
- Focus on Supply Chain Security: Attacks on software vendors can compromise a large number of end customers simultaneously. Strengthening security in the software supply chain is critical.
Conclusion: A Constant Vigilance
Defending against ransomware is not a one-time effort but a continuous process of vigilance, adaptation, and improvement. By adopting a layered defense strategy, staying informed about the latest threats, and investing in security awareness and training, organizations can significantly reduce their risk of falling victim to this relentless and evolving adversary. The fight against ransomware requires a proactive, informed, and adaptable approach – one that prioritizes prevention, detection, and rapid response. Only through this commitment can we hope to safeguard our digital world and preserve our data from the clutches of ransomware.
Additional Information
The Rise of Ransomware: A Deep Dive into the Growing Threat and Defense Strategies
Ransomware, a type of malicious software designed to block access to a computer system or data until a sum of money is paid, has exploded in both frequency and sophistication. It’s no longer just a nuisance; it’s a multi-billion dollar global industry, crippling organizations of all sizes and impacting critical infrastructure. Understanding the nuances of this evolving threat is paramount to developing robust defenses.
I. The Anatomy of a Ransomware Attack:
A typical ransomware attack follows a multi-stage process:
- Initial Access: Attackers gain initial access to the target network. This can be achieved through various methods:
- Phishing: Deceptive emails or messages lure victims into clicking malicious links or opening infected attachments. This is a primary entry point.
- Exploiting Vulnerabilities: Attackers identify and exploit known security flaws (e.g., unpatched software, outdated operating systems) to gain unauthorized access. Zero-day exploits (previously unknown vulnerabilities) are particularly potent.
- Credential Theft: Gaining access to valid user credentials through techniques like password spraying (trying common passwords) or brute-force attacks.
- Malvertising: Injecting malicious code into legitimate advertising networks to spread malware to websites visited by potential victims.
- Supply Chain Attacks: Targeting a third-party vendor or service provider with access to the target’s network. This provides a single point of entry to compromise multiple organizations.
- Lateral Movement: Once inside the network, attackers move laterally, gaining access to more systems and escalating their privileges. This involves:
- Scanning the Network: Discovering connected devices, identifying valuable data, and mapping out the network infrastructure.
- Privilege Escalation: Gaining higher-level permissions to access more sensitive data and control critical systems.
- Credential Harvesting: Stealing credentials (usernames, passwords, API keys) from compromised systems to gain further access and control.
- Data Exfiltration (Optional, but Increasingly Common): Before encrypting data, attackers often exfiltrate (steal) sensitive data and threaten to leak it publicly or sell it if the ransom isn’t paid. This tactic, known as “double extortion,” significantly increases the pressure to pay the ransom.
- Encryption: The ransomware encrypts the targeted data (files, databases, entire drives), rendering it inaccessible to the victim. Sophisticated ransomware variants use strong encryption algorithms to make decryption extremely difficult without the decryption key controlled by the attackers.
- Ransom Demand: The attackers leave a ransom note instructing the victim on how to pay the ransom, often specifying the amount, the payment method (typically cryptocurrency like Bitcoin), and a deadline.
- Negotiation (Optional): Some ransomware groups allow victims to negotiate the ransom amount.
- Decryption (Hopefully): If the ransom is paid (and there’s no guarantee the attackers will provide a working decryption key), the attackers provide the decryption key or software to unlock the data.
II. Types of Ransomware and Trends:
- Crypto-ransomware: Encrypts files and demands payment for decryption. This is the most common type.
- Locker ransomware: Locks the victim out of their system but doesn’t necessarily encrypt files.
- Double Extortion Ransomware: Steals data before encryption and threatens to release or sell it if the ransom isn’t paid. This has become the dominant tactic.
- Ransomware-as-a-Service (RaaS): Cybercriminals offer ransomware kits and infrastructure to other individuals, making it easier for less technically skilled attackers to launch attacks. This has led to an explosion in the number of attacks.
- Targeted Ransomware: Attacks that are specifically designed to target a particular organization or industry, often involving significant reconnaissance and tailored malware.
- Multi-Stage Attacks: Combining ransomware with other malicious activities like botnet creation or data theft.
- Mobile Ransomware: Targeting mobile devices (smartphones, tablets) and increasingly, mobile app developers.
- Evolving Tactics: Ransomware is constantly evolving. Attackers are now:
- Targeting backups: Attempting to disable or delete backups to prevent data recovery.
- Using more sophisticated obfuscation techniques: Making malware harder to detect and analyze.
- Exploiting vulnerabilities in cloud environments: Targeting cloud storage and infrastructure.
III. Industries Most at Risk:
While all industries are vulnerable, some are particularly attractive targets for ransomware attacks due to the potential for high ransoms and business disruption:
- Healthcare: Patient data is highly valuable, and disruptions to medical services can be life-threatening.
- Financial Services: Large sums of money are at stake, and any disruption can have significant financial consequences.
- Manufacturing: Operational technology (OT) and industrial control systems (ICS) are increasingly connected and vulnerable. Disrupting production can be extremely costly.
- Government: Government agencies hold sensitive data and provide essential services, making them attractive targets.
- Education: Universities and schools often have large networks and valuable research data.
- Critical Infrastructure: Energy, water, and transportation systems are attractive targets, as disrupting them can have widespread consequences.
- Legal Firms: Holding highly sensitive client information.
IV. Defending Against Ransomware: A Multi-Layered Approach:
Effective ransomware defense requires a comprehensive, multi-layered strategy that addresses all stages of the attack lifecycle. It’s not just about technology; it’s also about people and processes. Key components include:
-
Proactive Security Measures:
- Vulnerability Management: Regularly scan for and patch software vulnerabilities, including operating systems, applications, and firmware. Implement a vulnerability management program that prioritizes critical vulnerabilities.
- Endpoint Detection and Response (EDR): Deploy EDR solutions that provide real-time threat detection, investigation, and response capabilities on endpoints (laptops, desktops, servers). EDR solutions use behavioral analysis, machine learning, and threat intelligence to identify malicious activity.
- Network Segmentation: Divide the network into smaller, isolated segments to limit the impact of a breach. This prevents attackers from easily moving laterally.
- Least Privilege: Grant users and systems only the minimum necessary access rights. This limits the damage an attacker can inflict if credentials are compromised.
- Strong Authentication: Implement multi-factor authentication (MFA) for all critical systems, including email, VPNs, and cloud services. MFA makes it much harder for attackers to gain access even if they steal credentials.
- Regular Security Audits and Penetration Testing: Conduct regular security assessments, including penetration testing, to identify weaknesses in the security posture. Simulate real-world attacks to evaluate the effectiveness of security controls.
- Threat Intelligence: Subscribe to threat intelligence feeds to stay informed about emerging ransomware threats, tactics, and indicators of compromise (IOCs). This helps proactively identify and block malicious activity.
- Security Awareness Training: Train employees to recognize and avoid phishing attacks, social engineering, and other common attack vectors. Regular training and simulated phishing campaigns are essential.
- Email Security: Implement robust email security solutions to filter out malicious emails, including phishing attempts and emails containing malware. Consider solutions that offer advanced threat detection, sandboxing, and link protection.
-
Detection and Incident Response:
- Security Information and Event Management (SIEM): Deploy a SIEM solution to collect and analyze security logs from across the network. SIEMs provide centralized visibility into security events, enabling faster detection of suspicious activity and correlation of events.
- Network Intrusion Detection and Prevention Systems (IDS/IPS): Deploy IDS/IPS solutions to monitor network traffic for malicious activity and block known attacks.
- Behavioral Analysis: Implement tools that analyze user and system behavior to detect anomalies that could indicate a ransomware attack (e.g., unusual file access patterns, mass file encryption).
- Incident Response Plan: Develop and regularly test a detailed incident response plan that outlines the steps to take in the event of a ransomware attack. This plan should include:
- Containment: Isolating infected systems to prevent the spread of ransomware.
- Eradication: Removing the ransomware from infected systems.
- Recovery: Restoring data from backups.
- Post-Incident Analysis: Identifying the root cause of the attack and implementing measures to prevent future incidents.
- Backup and Recovery: Implement a robust and regularly tested backup and recovery strategy:
- Regular Backups: Back up all critical data regularly (daily or more frequently).
- Offsite/Offline Backups: Store backups offsite or offline to protect them from ransomware attacks that target the network. Consider air-gapped backups (disconnected from the network).
- Immutable Backups: Use immutable backups that cannot be altered or deleted by attackers.
- Backup Testing: Regularly test the backup and recovery process to ensure that data can be restored quickly and effectively.
- Threat Hunting: Proactively search for threats within the network, even if there are no alerts.
-
Response and Mitigation:
- Containment: Immediately isolate infected systems and network segments to prevent the ransomware from spreading.
- Identify the Ransomware Variant: Determine the specific ransomware variant to understand its behavior and identify potential decryption tools.
- Assess the Damage: Determine the scope of the attack, including which systems and data have been affected.
- Decryption (If Possible): Explore available decryption tools. Some ransomware variants have known vulnerabilities that allow for decryption. Check resources like No More Ransom (a joint initiative by law enforcement and cybersecurity companies) for potential decryption keys.
- Negotiation (Consider Carefully): Consider the risks and benefits of negotiating with the attackers. Paying the ransom does not guarantee that the data will be recovered, and it encourages further attacks. Consult with legal counsel and cybersecurity experts before making a decision.
- Notify Law Enforcement: Report the ransomware attack to the appropriate law enforcement authorities. They can investigate the incident and potentially help to identify and apprehend the attackers. Also, consider reporting to your industry’s reporting and analysis organizations.
- Communicate: Communicate with stakeholders (employees, customers, partners) about the incident. Transparency is crucial, but also consider the potential for legal implications.
- Restore from Backups: The most effective way to recover from a ransomware attack is to restore data from clean backups. This is why a robust backup and recovery strategy is so critical.
- Post-Incident Review: Conduct a thorough post-incident review to identify lessons learned and implement measures to improve the security posture.
V. Emerging Technologies and Strategies:
- AI-Powered Security: Machine learning and artificial intelligence are being used to enhance threat detection, improve incident response, and automate security tasks.
- Zero Trust Security: A security model that assumes no user or system is trustworthy by default. It requires all users and systems to be continuously verified before granting access to resources.
- Extended Detection and Response (XDR): Integrates security data from various sources (endpoints, networks, cloud) to provide a more holistic view of threats and improve detection and response capabilities.
- Deception Technology: Deploying honeypots and decoys to lure attackers and detect their presence within the network.
- Cyber Insurance: Consider obtaining cyber insurance to help cover the costs of a ransomware attack, including incident response, data recovery, and legal fees. Cyber insurance policies often require organizations to implement specific security controls.
VI. Key Takeaways:
- Ransomware is a serious and evolving threat that requires a proactive and comprehensive defense.
- A layered approach that combines technology, people, and processes is essential.
- Regularly patch vulnerabilities, implement strong authentication, and backup data regularly.
- Develop and test an incident response plan.
- Stay informed about the latest ransomware threats and tactics.
- Consider the legal and ethical implications of responding to a ransomware attack.
- Cybersecurity is not a one-time project but a continuous process of improvement.
By implementing these strategies, organizations can significantly reduce their risk of becoming victims of ransomware and minimize the impact of an attack if one occurs. Staying vigilant, investing in security, and fostering a security-conscious culture are crucial for defending against this persistent and evolving threat.




