The Ultimate Guide to Cybersecurity: Fortifying Your Digital Fortress
The digital realm, once a shimmering promise of boundless connection, has become a double-edged sword. While it offers unprecedented convenience and access, it also harbors unseen threats. From malicious actors seeking to steal your identity to state-sponsored cyberattacks aimed at destabilizing nations, the dangers are real and ever-evolving. This guide serves as your blueprint, your digital survival manual, for navigating this complex landscape and erecting a formidable defense against cyber threats.
Chapter 1: Understanding the Enemy: Cyber Threats Demystified
Before we can build our fortress, we must understand the attackers and their weapons. The cyber threat landscape is vast, but understanding the core categories is crucial.
Common Cyber Threats: A Rogue’s Gallery
| Threat Type | Method of Attack | Impact |
|---|---|---|
| Malware | Viruses, Trojans, Worms, Ransomware, Spyware | Data theft, system damage, financial loss, espionage |
| Phishing | Deceptive emails, messages, or websites | Identity theft, credential compromise, malware infection |
| Social Engineering | Manipulating individuals to reveal sensitive information | Data breaches, financial fraud |
| Man-in-the-Middle (MITM) | Intercepting communication between two parties | Data interception, eavesdropping, theft |
| Denial-of-Service (DoS/DDoS) | Overwhelming a system with traffic | Service disruption, business downtime |
| Insider Threats | Malicious or negligent actions by employees/contractors | Data leakage, sabotage, espionage |
| Advanced Persistent Threats (APTs) | Sophisticated, long-term attacks by nation-states or groups | Espionage, sabotage, large-scale data breaches |
These threats are constantly evolving, morphing, and adapting. Staying informed about the latest tactics and trends is vital for maintaining robust security.
Chapter 2: Building Your Digital Fortress: The Pillars of Cybersecurity
Effective cybersecurity is not a single solution; it’s a layered approach. Think of your digital fortress as having multiple defensive walls. Here are the foundational pillars:
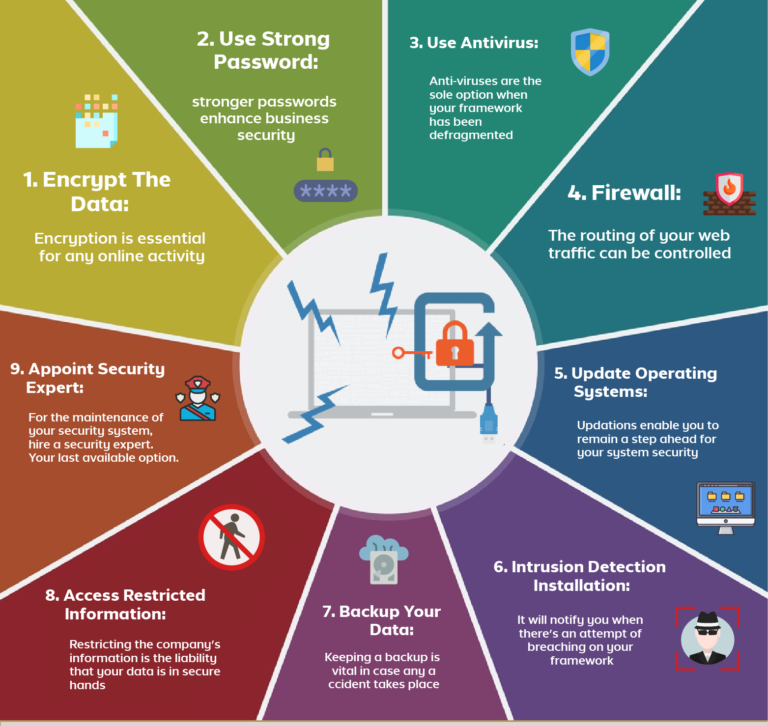
Pillar 1: Strong Passwords and Authentication
Your password is the first line of defense. Don’t treat it lightly!
- Password Strength: Use long, complex passwords. Aim for at least 12 characters, combining uppercase and lowercase letters, numbers, and symbols. Avoid dictionary words, personal information, and sequential patterns.
- Password Management: Employ a password manager to securely store and generate unique, complex passwords for each of your accounts.
- Multi-Factor Authentication (MFA): Enable MFA whenever possible. This adds an extra layer of security by requiring a second form of verification, such as a code from your phone, in addition to your password.
- Regular Password Changes: While not always necessary, changing passwords periodically, especially for high-value accounts, can reduce your attack surface.
Pillar 2: Software Updates & Patching
Software vulnerabilities are a cybercriminal’s playground. Keep your systems patched!
- Automated Updates: Enable automatic updates for your operating systems, web browsers, antivirus software, and other applications. This ensures you receive the latest security patches.
- Regular Manual Checks: Even with automated updates, periodically check for updates manually to ensure everything is current.
- End-of-Life (EOL) Software: Avoid using software that is no longer supported by the vendor. EOL software does not receive security patches, leaving it highly vulnerable.
Pillar 3: Network Security: Fortifying the Perimeter
Your network is the gateway to your digital life. Protect it!
- Firewall: Use a firewall to control network traffic and block unauthorized access. This acts as a barrier between your network and the outside world.
- Wireless Security: Secure your Wi-Fi network with a strong password (WPA3 is recommended) and hide your network name (SSID).
- VPN (Virtual Private Network): Use a VPN, especially when using public Wi-Fi, to encrypt your internet traffic and mask your IP address.
- Network Segmentation: Separate your network into different segments to limit the impact of a potential breach. For example, isolate your guest Wi-Fi from your internal network.
Pillar 4: Data Encryption: Protecting Your Treasures
Encryption scrambles data, rendering it unreadable to unauthorized parties.
- Full Disk Encryption: Encrypt your hard drives and SSDs to protect your data if your device is lost or stolen.
- File Encryption: Encrypt sensitive files and folders to prevent unauthorized access.
- Secure Communication: Use encrypted email services and messaging apps to protect your communications.
- HTTPS: Always use websites that start with “HTTPS” (Hypertext Transfer Protocol Secure) to ensure that your data is encrypted during transmission.
Pillar 5: Awareness and Education: The Human Firewall
Humans are often the weakest link. Training and awareness are paramount.
- Phishing Awareness Training: Educate yourself and your employees (if applicable) about phishing tactics and how to identify suspicious emails and links.
- Social Engineering Awareness: Understand social engineering techniques and how attackers manipulate individuals to reveal sensitive information.
- Safe Browsing Practices: Be cautious about clicking on links, downloading files, and visiting untrusted websites.
- Regular Cybersecurity Training: Participate in ongoing cybersecurity training to stay informed about the latest threats and best practices.
Chapter 3: Defending Against Specific Attacks: Tactical Maneuvers
Beyond the core pillars, you need to employ specific defenses against common attacks.
Defending Against Malware
- Antivirus Software: Install reputable antivirus software and keep it updated.
- Anti-Malware Scans: Regularly scan your devices for malware.
- Beware of Suspicious Files: Don’t open attachments or click on links from unknown senders.
- Backups: Regularly back up your data to a separate, secure location. This is your lifeline in case of a ransomware attack.
Combating Phishing
- Verify Sender Identity: Carefully examine the sender’s email address and look for suspicious signs.
- Inspect Links: Hover your mouse over links to see the actual URL before clicking.
- Be Wary of Urgency: Phishing emails often create a sense of urgency to pressure you into taking action.
- Report Suspicious Emails: Report phishing emails to the relevant authorities or your IT department.
Protecting Against Social Engineering
- Verify Requests: Always verify requests for information or access, especially those from people you don’t know.
- Be Skeptical: Don’t trust everything you see or hear, especially online.
- Protect Personal Information: Be cautious about sharing personal information online or over the phone.
- Question Authority: Don’t blindly trust individuals claiming to be in positions of authority.
Chapter 4: Disaster Recovery: Preparing for the Worst
Even with the best defenses, breaches can happen. Prepare for it.
The Backup Strategy
- Regular Backups: Implement a regular backup schedule (daily, weekly, or monthly, depending on your needs).
- Offsite Backups: Store backups offsite, such as in the cloud or on a separate hard drive, to protect against physical disasters.
- Test Backups: Regularly test your backups to ensure they are working correctly and that you can restore your data.
- Types of Backups: Understand the different backup types (full, incremental, differential) and choose the right strategy for your needs.
Incident Response Plan
- Define Roles and Responsibilities: Clearly define the roles and responsibilities of individuals in the event of a security incident.
- Containment: Have procedures in place to contain the incident and prevent further damage.
- Eradication: Identify and remove the cause of the incident.
- Recovery: Restore systems and data from backups.
- Post-Incident Analysis: Analyze the incident to identify lessons learned and improve your security posture.
Chapter 5: Cybersecurity for the Future: Adapting to Change
Cybersecurity is not a static field. It’s constantly evolving.
Emerging Threats
- AI-Powered Attacks: Artificial intelligence is being used to create more sophisticated and targeted attacks.
- IoT (Internet of Things) Vulnerabilities: The proliferation of IoT devices creates new attack vectors.
- Cloud Security: Secure cloud environments are critical, as organizations increasingly move their data and applications to the cloud.
Future-Proofing Your Defenses
- Stay Informed: Continuously educate yourself about the latest threats and technologies.
- Adopt Zero-Trust Architecture: Implement a zero-trust security model, which assumes no user or device is inherently trustworthy.
- Embrace Automation: Automate security tasks to improve efficiency and reduce human error.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and assess your security posture.
Conclusion: The Ongoing Journey
Cybersecurity is not a destination, but a continuous journey. By implementing the strategies and practices outlined in this guide, you can build a robust digital fortress, protect your data, and navigate the ever-changing cyber landscape with confidence. Remain vigilant, stay informed, and adapt to the evolving threats. Your digital future depends on it.

Additional Information
Okay, let’s dive into a detailed analysis of “The Ultimate Guide to Cybersecurity: How to Protect Your Data.” Since I don’t have access to a specific published guide with that exact title, I’ll analyze a hypothetical one, synthesizing common themes, essential topics, and best practices typically found in comprehensive cybersecurity guides for the average user or small business.
I. Core Themes and Overall Goals:
- Empowerment and Education: The primary goal of such a guide is to demystify cybersecurity and empower readers to take proactive steps to protect their data and digital lives. It aims to transform fear and uncertainty into knowledge and action.
- Practicality and Actionability: The content is designed to be practical. It shouldn’t be overly technical or theoretical, but provide concrete steps, checklists, and recommendations that individuals and businesses can immediately implement.
- Proactive vs. Reactive: The guide stresses the importance of proactive measures. It moves beyond simply responding to attacks and focuses on building a strong security posture to prevent them in the first place.
- Risk-Based Approach: The guide likely emphasizes that cybersecurity is about managing risks rather than achieving perfect security. It helps readers identify their biggest vulnerabilities and prioritize protections accordingly.
- Holistic Security: It acknowledges that cybersecurity isn’t just about technology. It covers technical, behavioral, and organizational aspects.
II. Key Content Areas and Detailed Analysis:
Here’s a breakdown of the common topics and how they are typically addressed in a comprehensive guide:
- Understanding the Threat Landscape:
- What are the threats?:
- Malware: Viruses, Trojans, ransomware, spyware, adware, and their evolving forms.
- Phishing and Social Engineering: Deceptive techniques to trick users into revealing sensitive information (passwords, financial data, etc.). Examples: spear phishing, whaling.
- Data Breaches: Unauthorized access and disclosure of data from websites, databases, and other systems.
- Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) Attacks: Disrupting access to websites and online services.
- Insider Threats: Malicious or unintentional actions by employees or contractors.
- Hardware Attacks: Physical theft of devices, tampering, or vulnerabilities.
- IoT Device Vulnerabilities: Security flaws in connected devices like smart home appliances, wearables, and industrial control systems.
- Supply Chain Attacks: Targeting vulnerabilities in third-party software or hardware vendors.
- Who are the attackers?: Hackers, cybercriminals, nation-state actors, and other malicious actors. Understanding their motivations (financial gain, espionage, sabotage, etc.) is important.
- How are attacks evolving?: The guide should stay updated on the latest trends and techniques, emphasizing things like:
- The use of AI and machine learning by attackers to automate attacks and make them more effective.
- Ransomware-as-a-Service (RaaS) and the professionalization of cybercrime.
- The increasing sophistication of social engineering tactics.
- What are the threats?:
- Password Management and Authentication:
- Strong Password Creation: Principles of creating strong, unique passwords. Examples:
- Length (12+ characters).
- Use of a mix of uppercase and lowercase letters, numbers, and symbols.
- Avoiding easily guessable information (birthdays, names, etc.).
- Password Managers: Highly recommended for storing and managing passwords securely. Benefits:
- Generating strong, random passwords.
- Storing passwords securely with encryption.
- Automatically filling in passwords on websites and apps.
- Multi-Factor Authentication (MFA): Critical for adding an extra layer of security to accounts. Types:
- Two-Factor Authentication (2FA): Combining a password with a code sent to a phone or email.
- Biometric authentication: Fingerprint, facial recognition, etc.
- Hardware security keys: (e.g., YubiKey) – Physical devices that provide strong authentication.
- Password Hygiene:
- Never reusing passwords across multiple accounts.
- Changing passwords regularly (or, realistically, less often but when there’s a potential breach).
- Avoiding storing passwords in insecure places (e.g., text files, sticky notes).
- Being cautious when responding to password reset requests.
- Strong Password Creation: Principles of creating strong, unique passwords. Examples:
- Device Security:
- Operating System (OS) Security:
- Keeping the OS updated: Critical for patching security vulnerabilities.
- Using a reputable antivirus/anti-malware solution: Regularly scanning for threats, including real-time protection.
- Firewall configuration: Configuring the OS firewall to block unwanted network traffic.
- User Account Control (UAC) settings: Protecting against unauthorized software installation and changes on Windows.
- Mobile Device Security (Smartphones & Tablets):
- Secure Lock Screen: Setting a strong passcode, PIN, or biometric authentication.
- App Security: Only installing apps from reputable sources (App Store, Google Play). Checking app permissions carefully.
- Mobile Device Management (MDM) for Businesses: Allows IT departments to manage and secure mobile devices used by employees.
- Keeping the OS and apps updated.
- Enabling “Find My Device” features for tracking and remote wiping in case of loss or theft.
- Avoiding public Wi-Fi networks or using a VPN.
- Laptop and Desktop Security: Following similar principles to mobile devices.
- IoT Device Security:
- Changing default passwords on all IoT devices.
- Keeping firmware updated.
- Segmenting the network to isolate IoT devices from more sensitive devices.
- Considering the security implications before purchasing an IoT device.
- Physical Security:
- Protecting devices from theft.
- Using screen locks when leaving devices unattended.
- Securely disposing of old hard drives and other storage media.
- Operating System (OS) Security:
- Network Security:
- Home Router Security:
- Changing the default router password.
- Enabling WPA3 encryption (the most secure option) or WPA2.
- Updating the router firmware.
- Disabling unnecessary features (e.g., UPnP).
- Configuring a guest network.
- Wi-Fi Security Best Practices:
- Avoiding public Wi-Fi unless absolutely necessary.
- Using a Virtual Private Network (VPN) when using public Wi-Fi. A VPN encrypts your internet traffic, protecting it from eavesdropping.
- Being wary of suspicious Wi-Fi network names.
- Understanding Network Segmentation: Dividing your network into different segments to limit the impact of a breach.
- Firewalls: Understanding how firewalls work and their role in blocking unauthorized network traffic.
- Home Router Security:
- Email Security:
- Phishing Awareness:
- Recognizing phishing emails: Spoofed sender addresses, suspicious links, urgent requests, grammatical errors.
- Hovering over links before clicking them to see the actual destination URL.
- Never clicking on links or downloading attachments from unknown senders.
- Reporting phishing attempts.
- Email Security Settings:
- Enabling spam filters.
- Using a reputable email provider with good security features.
- Being careful about the information shared in email signatures.
- Avoiding sending sensitive information via email unless it is encrypted.
- Phishing Awareness:
- Web Browsing Security:
- Safe Browsing Habits:
- Being wary of suspicious websites.
- Checking for the “https” prefix and a padlock icon in the address bar.
- Avoiding clicking on pop-up ads.
- Not downloading files from untrusted sources.
- Browser Security Settings:
- Keeping the browser updated.
- Enabling security features in the browser (e.g., safe browsing mode).
- Using a browser extension to block ads and trackers.
- Understanding cookies and privacy settings.
- Safe Browsing Habits:
- Data Backup and Recovery:
- Importance of Backups: A critical defense against ransomware, data loss, hardware failure, and accidental deletion.
- Types of Backups:
- Full Backups: Copying all data.
- Incremental Backups: Copying only the data that has changed since the last backup.
- Differential Backups: Copying data changed since the last full backup.
- Backup Strategies:
- The 3-2-1 Rule: 3 copies of data, on 2 different media, with 1 offsite (cloud or physically separate location).
- Automated Backups: Setting up scheduled backups to minimize the risk of forgetting.
- Testing Backups Regularly: Verifying that data can be restored successfully.
- Cloud Backup Services: Advantages, disadvantages, and how to choose a reputable service.
- Social Engineering and Human Behavior:
- Recognizing Social Engineering Tactics: Understanding how attackers exploit human psychology to gain access to information or systems.
- Training and Awareness: Educating users about common social engineering techniques and how to avoid them.
- Policies and Procedures: Establishing clear guidelines for employees on how to handle sensitive information, passwords, and security incidents.
- Security Awareness Training: Periodic training sessions, quizzes, and simulated phishing attacks to reinforce security best practices.
- Privacy and Data Protection:
- Understanding Your Privacy Rights: Knowing your rights under data protection regulations (e.g., GDPR, CCPA, etc.).
- Privacy Settings: Adjusting privacy settings on social media platforms, search engines, and other online services.
- Minimizing Data Collection: Being mindful of the information you share online and limiting the amount of personal data collected by websites and apps.
- Privacy-Enhancing Technologies (PETs):
- VPNs (Virtual Private Networks): As discussed above.
- Tor Browser: A browser that routes your internet traffic through a network of relays to anonymize your browsing activity.
- Privacy-focused search engines: (e.g., DuckDuckGo).
- Encrypted messaging apps: (e.g., Signal, Wire).
- Incident Response:
- Planning for a Security Incident: Developing a plan for how to respond to a security breach or other security incident.
- Incident Response Steps:
- Identification: Detecting and confirming the incident.
- Containment: Limiting the damage (e.g., isolating infected devices).
- Eradication: Removing the threat (e.g., deleting malware, patching vulnerabilities).
- Recovery: Restoring systems and data.
- Lessons Learned: Analyzing the incident to identify areas for improvement.
- Reporting Security Incidents: Knowing how to report incidents to the appropriate authorities.
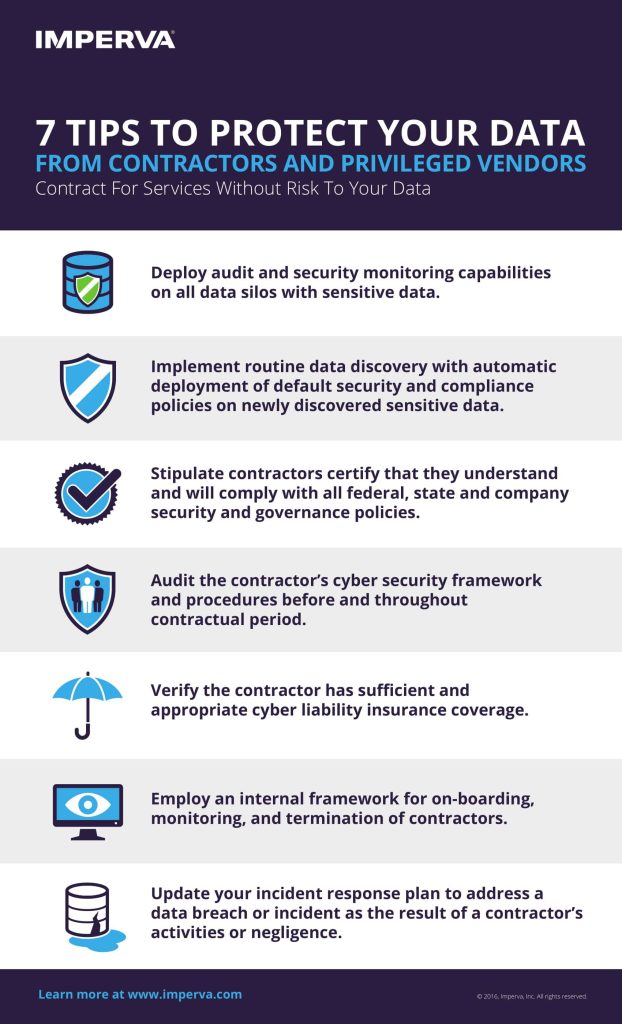
- For Businesses and Organizations:
- Security Policies and Procedures: Developing and implementing comprehensive security policies.
- Employee Training and Awareness: Providing regular security training for all employees.
- Access Control: Limiting access to sensitive data and systems based on the principle of least privilege.
- Vulnerability Management: Identifying and patching security vulnerabilities in software and hardware.
- Network Monitoring: Monitoring network traffic for suspicious activity.
- Security Audits and Assessments: Regularly evaluating the effectiveness of security controls.
- Cybersecurity Insurance: Considering insurance to help cover the costs of a data breach.
- Resources and Further Learning:
- Links to reputable websites and organizations: (e.g., NIST, CISA, SANS Institute, OWASP).
- Books and articles: Recommending further reading on specific topics.
- Tools and software: Suggesting useful tools for security testing, password management, and other tasks.
- Cybersecurity certifications: Informing readers of potential certifications to explore.
III. Additional Considerations and Best Practices:
- Regular Updates: Emphasize that cybersecurity is an ongoing process, not a one-time activity.
- Customization: The guide should provide enough flexibility to be tailored to different user types and risk profiles.
- Plain Language: Avoid overly technical jargon and explain concepts clearly.
- Visual Aids: Use images, diagrams, and checklists to make the information more accessible and engaging.
- Real-World Examples and Scenarios: Provide examples of how threats manifest in real-world situations.
- Call to Action: Encourage readers to take immediate steps to improve their security.
IV. Conclusion:
“The Ultimate Guide to Cybersecurity: How to Protect Your Data” (in the hypothetical sense) would be a valuable resource for anyone who wants to understand and improve their cybersecurity posture. It’s a guide that helps individuals, small businesses, and even larger organizations reduce their risks and protect their most valuable assets in the digital age. It’s a living document that needs to be updated frequently because the threat landscape changes constantly. The goal is to foster a culture of cybersecurity awareness and proactive security measures to keep users safe online.