The Fortress of You: Why Multi-Factor Authentication is Your Digital Bodyguard
Our digital lives are shimmering tapestries woven with threads of personal data, financial transactions, and intimate communications. Each click, like a tiny brushstroke, contributes to the masterpiece of our online identity. But just as any masterpiece can be threatened by theft or vandalism, so too is our online presence vulnerable to malicious actors. Enter Multi-Factor Authentication (MFA) – the digital bodyguard safeguarding your precious online realm.
The Single Gatekeeper: Why Passwords Aren’t Enough
Imagine your online accounts as fortresses, and your password the single gatekeeper. A strong password, carefully crafted with a blend of upper and lowercase letters, numbers, and symbols, is undoubtedly a sturdy lock. However, the digital landscape has evolved. Sophisticated hackers employ increasingly cunning methods to bypass even the strongest locks.
- Phishing Attacks: Deceptive emails or websites mimicking legitimate services trick you into revealing your password.
- Malware: Malicious software installed on your device can capture your keystrokes, including your precious password.
- Data Breaches: Companies holding vast troves of personal data are occasionally breached, exposing user credentials to the dark web.
A compromised password alone grants access to your digital life, akin to handing the key to your fortress directly to the enemy. This is where MFA steps in, transforming your single gatekeeper into a layered defense.
Multi-Factor Authentication: Layers of Defense
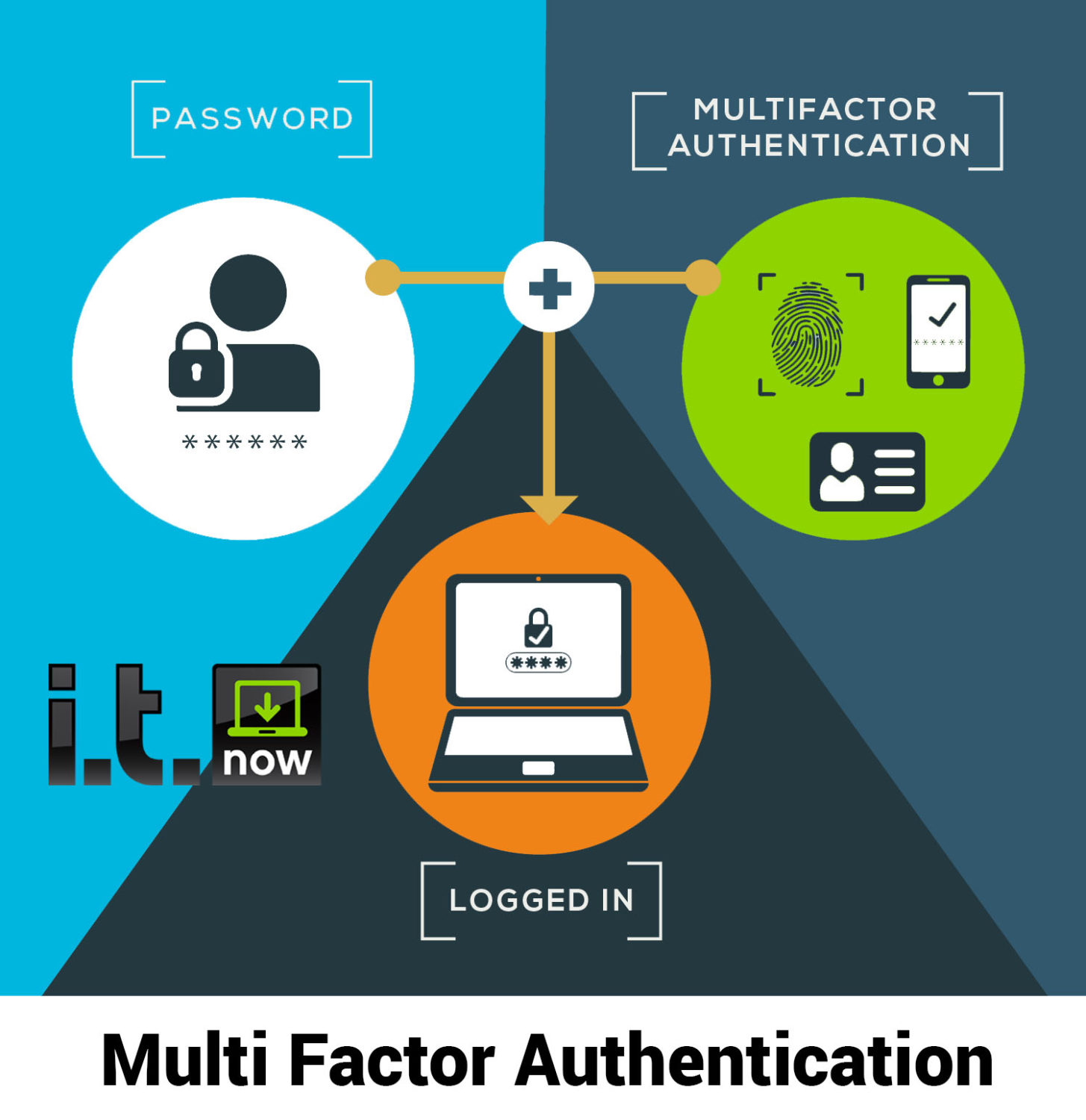
MFA adds an extra layer, or several layers, of security to your online accounts. Think of it as a key combined with an access code, or a physical key that needs a thumbprint before opening the door. It requires you to verify your identity using two or more independent factors. These factors typically fall into the following categories:
| Factor Type | Description | Examples |
|---|---|---|
| Something You Know | Information you are familiar with. | Password, PIN, security questions (though security questions are generally less secure). |
| Something You Have | Physical item you possess. | Smartphone (for code generation or push notifications), hardware security key (e.g., YubiKey). |
| Something You Are | Your unique biological characteristics. | Biometrics – fingerprints, facial recognition, voice recognition (becoming increasingly common on devices). |
By requiring multiple factors, MFA makes it significantly harder for unauthorized individuals to gain access, even if they have managed to steal your password.
The MFA Arsenal: Common Implementations
Several MFA implementations are widely used and readily available. Familiarizing yourself with these options will help you choose the best defense strategy.
1. Time-Based One-Time Passwords (TOTP)
- How it works: An app (e.g., Google Authenticator, Authy) on your smartphone generates a unique, time-sensitive code that you enter along with your password.
- Strength: Strong, as the code is only valid for a short period.
- Ease of Use: Requires an app, but generally simple to set up and use.
2. SMS-Based Codes
- How it works: A unique code is sent to your registered mobile number via SMS (text message).
- Strength: Relatively secure, but vulnerable to SIM swapping attacks.
- Ease of Use: Simple, but less secure than TOTP or hardware keys.
3. Push Notifications
- How it works: You receive a notification on your smartphone, prompting you to approve or deny the login attempt.
- Strength: Convenient and relatively secure.
- Ease of Use: Very easy to use; requires a smartphone and the relevant app.
4. Hardware Security Keys
- How it works: A physical device (e.g., a USB key) plugs into your computer and authenticates you with a tap or button press.
- Strength: Extremely secure, offering strong protection against phishing and other attacks.
- Ease of Use: Requires purchasing a hardware key, but usage is typically straightforward.
Beyond the Basics: Strengthening Your MFA Strategy
Implementing MFA is a vital first step, but maximizing its effectiveness requires careful planning and a proactive approach.
- Prioritize the Strongest Methods: Choose TOTP or hardware security keys over SMS-based codes whenever possible.
- Enable MFA Everywhere: Activate MFA on all your critical accounts, including email, banking, social media, and cloud storage.
- Regularly Review Your Security Settings: Ensure that your recovery options are up-to-date and that you have access to your backup codes.
- Stay Vigilant: Be wary of phishing attempts, even if they appear to come from legitimate sources. Double-check URLs and be cautious about clicking suspicious links.
- Educate Yourself: Continuously learn about emerging security threats and the latest MFA best practices.
The Future of MFA: Biometrics and Beyond
The evolution of MFA is accelerating, with exciting advancements promising even greater security and convenience.
- Biometric Authentication: Fingerprint, facial, and voice recognition are becoming increasingly integrated into smartphones and other devices, offering a seamless and secure way to verify your identity.
- Behavioral Biometrics: Analyzing how you type, how you move your mouse, and other behavioral patterns can identify you even when you are on an unfamiliar device.
- Passwordless Authentication: The goal is a future where passwords become relics of the past, replaced by more robust and user-friendly authentication methods.
Embrace the Fortress Within
Multi-Factor Authentication is not just a security measure; it’s an investment in your digital well-being. It is the digital bodyguard standing between your valuable data and the ever-present threats of the online world. Embracing MFA is empowering, giving you control over your digital identity and a sense of confidence as you navigate the online realm. Make the choice today. Fortify your digital fortress. Secure the You within.

Additional Information
Why Multi-Factor Authentication (MFA) is Crucial for Online Security: A Deep Dive
Multi-Factor Authentication (MFA) is no longer a luxury; it’s a necessity for robust online security. It adds an extra layer of protection beyond just a username and password, making it significantly harder for unauthorized individuals to access your accounts and sensitive information. Here’s a detailed breakdown of why MFA is crucial:
1. Mitigation Against Password-Related Vulnerabilities:
- Password Complexity Failures: Humans are notoriously bad at creating and remembering strong, unique passwords. They often resort to weak, easily guessable passwords (e.g., “password123,” birthdays, names) or reuse the same password across multiple accounts. This makes them vulnerable to:
- Brute-force attacks: Automated programs systematically try different password combinations.
- Dictionary attacks: Attempting passwords from a pre-compiled list of common passwords.
- Credential stuffing: Hackers use stolen credentials from one breached service to try logging into others.
- Password Leaks and Breaches: Even strong passwords are at risk. Data breaches are common, exposing millions of usernames and passwords. If a service you use is compromised, your password, regardless of its strength, could be leaked and used for unauthorized access.
- Phishing Attacks: Sophisticated phishing attacks trick users into entering their credentials on fake websites that mimic legitimate ones. MFA renders these attacks far less effective, as the attacker still needs to obtain the second factor (e.g., a code from your phone).
2. The Power of Layered Security:
- Beyond a Single Point of Failure: MFA introduces multiple “factors” that must be verified to authenticate a user. These factors typically fall into three categories:
- Something you know: This is typically your password, but can also include security questions.
- Something you have: A physical device you possess, such as a smartphone with an authenticator app (Google Authenticator, Microsoft Authenticator), a security key (YubiKey), or a one-time password (OTP) sent via SMS.
- Something you are: Biometric authentication, such as fingerprint scanning, facial recognition, or voice recognition.
- Increased Resilience: Even if one factor is compromised (e.g., your password is stolen), the attacker still needs to overcome the other factors to gain access. This makes it significantly more difficult to breach an account. For instance, even if a hacker steals your password through a phishing attack, they will need access to your phone (or security key) to get the code needed for the second factor.
3. Specific Benefits and Analysis:
- Reduced Risk of Account Takeovers (ATO): ATOs are becoming increasingly common, and MFA is a powerful deterrent. Hackers often use stolen credentials to impersonate users and gain access to personal information, financial accounts, or sensitive corporate data. MFA significantly reduces the success rate of these attacks.
- Protection Against Malware and Ransomware: MFA can hinder attackers who use malware to steal credentials or lock you out of your systems with ransomware. If the malware only captures your password, the attacker still cannot log in without the second factor.
- Compliance and Regulatory Requirements: Many industries and regulatory bodies (e.g., HIPAA, GDPR, PCI DSS) now mandate or strongly recommend MFA to protect sensitive data. Implementing MFA helps organizations meet compliance requirements and avoid costly fines and penalties.
- Improved User Trust and Confidence: MFA demonstrates a commitment to security, which builds trust with customers and stakeholders. It provides users with a sense of security and control over their accounts.
- Mitigation of Insider Threats: In organizations, MFA can help protect against malicious insiders who may try to access sensitive data. Even with insider knowledge and a password, the attacker would still need access to the authorized device or biometric authentication.
- Combating Advanced Persistent Threats (APTs): APTs are sophisticated attacks by well-funded and highly skilled adversaries. While no security measure is foolproof, MFA significantly increases the complexity and time needed for an APT to succeed, potentially deterring them or at least providing more time for detection and response.
4. Considerations for Implementing MFA:
- Usability: MFA should be easy to use to encourage adoption. Poor user experience can lead users to disable MFA, defeating its purpose. Balance security with convenience. Consider using authenticator apps that generate codes automatically, rather than relying solely on SMS, which is vulnerable to SIM-swapping attacks.
- Factor Choice: Select the appropriate MFA factors based on your needs, the sensitivity of the data being protected, and the users’ technical capabilities. Security keys are considered the most secure factor, followed by authenticator apps, and then SMS.
- Recovery Mechanisms: Provide a secure and user-friendly recovery process in case a user loses access to their second factor (e.g., their phone). Options include backup codes, emergency access to an administrator, or multi-factor recovery.
- Cost-Benefit Analysis: Evaluate the cost of implementing and maintaining MFA against the potential losses from security breaches. While there is a cost associated with MFA (e.g., hardware, software, training), the long-term benefits of improved security and reduced risks far outweigh the investment.
- Training and Awareness: Educate users about the importance of MFA and how to use it effectively. Provide clear instructions and support to ensure widespread adoption.
- Phased Implementation: Consider a phased approach, starting with the most critical accounts and gradually expanding to others.
- Monitoring and Auditing: Continuously monitor and audit the effectiveness of your MFA implementation. Review logs for suspicious activity and adjust your security measures as needed.
In Conclusion:
Multi-Factor Authentication is no longer an optional security measure; it’s a fundamental requirement for protecting online accounts and sensitive data. By implementing MFA, you significantly reduce the risk of account compromises, data breaches, and financial losses. The benefits far outweigh the costs, making MFA an essential investment in a secure digital environment for both individuals and organizations. It is an effective and relatively easy-to-implement measure that provides substantial security improvements. Ignoring MFA is akin to leaving your front door unlocked – inviting trouble.